In Windows 8, as you know, there are two types account: local and, if I may say so, remote, that is, a Microsoft account.
This is exactly the case when the user’s data, his login and password for logging into the operating system are stored on the server. Of course, this does not mean that you will not be able to log in if your computer is not connected to the Internet.
On the contrary, using an account Microsoft records has a number of advantages, one of which is access to various remote services, for example, to the same Store, or rather to certain applications.
Password recovery using a Microsoft account
There is another important advantage of using a remote account. Imagine this situation. God knows how, but it just so happens that you lost your administrator password. If you are using a remote Microsoft account, you can reset your password in just a few clicks. You remember your Microsoft account login, address Email? From any work computer, go to the password reset page and follow the instructions to create New Password.To confirm the transaction, you will need to send the received message to mobile phone code or by answering a security question.
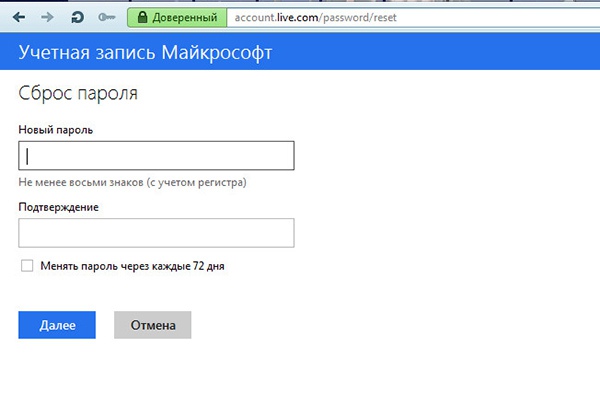
Microsoft account password reset page: https://account.live.com/password/reset
using a reset floppy
If you use a local account, things are a little more complicated. There are many ways to reset the administrator password in Windows 8, but we will look at only two of them. You can reset your password using a reset disk. The disadvantage of this method is that such a floppy disk should already be at hand.Create it as you should in advance. Consider this your insurance. The disk does not require eating, does not need maintenance, and in case of trouble it will come in handy.

It's very easy to create. Open Control Panel and go to the “User Accounts” section. Select the option “Create a password reset disk” and insert it into the USB connector. Following the wizard's instructions, write the necessary data onto the media.
If in the future you, insert your disk into the USB connector and click “Reset Password”. In the window that opens, enter a new password, confirm it, then enter a hint and save the result. The password will be changed.
Resetting your password using the installation disc
If you do not have a password reset floppy disk, but have a Windows 8 installation disk, you can try the following method. It is well known to many experienced users, detailed description This method can be found on the Internet, but we post it only for the sake of our regular readers. As you already understand, we will boot from installation disk. In the first dialog box with language selection options, press the key combination Shift + F10.

This will open a window command line. Next, you will need to identify the drive where Windows is installed. The point is in this case letter system disk differs from the letter that the system assigns to the partition. Typically, this is the letter D. To verify this, run the following command:

This will output the entire contents of the disk. If there are folders Windows, Program Files, etc., then you are on the right track.
And now we will need to do this trick - replace the sethc.exe or Utilman.exe file with the command line launch file. For what? Let's explain.
IN Windows file sethc.exe is responsible for sticky keys, the same one that turns on when you press the Shift key five times. The Utilman.exe file is the Ease of Access Center applet. So, when replacing any of these files with cmd.exe, when we try to run them, a command prompt window with SYSTEM rights will open, which gives us the opportunity to perform any operation in Windows without authorization, including changing the password.
First you need to create backup copy file sethc.exe and save it to any location convenient for you, for example like this:
copy d:windowsSystem32sethc.exe d:

Let's replace the sethc.exe file with the cmd.exe file. To confirm you will need to press Y:
copy d:windowsSystem32cmd.exe d:windowsSystem32sethc.exe

Now you need to restart your computer. This time in the BIOS we set the normal boot from hard drive, remove the installation disk from the drive. After a window appears with a password entry field that we do not know, you must quickly press the Shift key. This will launch the command line. We set the user a new password:
net user comp password


In this case, “compus” is the administrator’s name, and “password” is the new password. If the administrator's name consists of two parts separated by a space, for example “Ivan Ivanov”, it must be placed in quotes:
net user “Ivan Ivanov” password
That's all. Close the command line window and log in with the new password. If the account for which this trick was performed does not have administrator rights, add them manually by running the following command:
net localgroup administrators comp /add
The procedure when using the Utilman.exe file is practically no different from the example given, with the exception of the hot key. Instead of pressing Shift five times, you need to use the Win + U combination. And one last thing. To avoid possible security problems, you need to return everything to its place. Boot from the installation disk and, opening a command prompt window, run the command:
copy d:sethc.exe d:windowssystem32sethc.exe
The original sethc.exe file will be returned to its rightful place. As you can see, everything is quite simple. No hassle with special software and LiveCD, all you need is an installation disk with Windows 8. To the objection of what to do if this disk is not there, we will answer: find it on the Internet, download and burn the distribution kit of the corresponding Windows versions is not a problem, so there is no need to worry about the lack of an installation disk.
A standard situation is that the administrator has blocked many functions of the computer user. What to do, how to reset or find out the Windows administrator password? To reset or change the administrator password or Windows user There are many options available, one of which is the ERD Commander program. However, your interference with the security of your computer will be revealed immediately the next time you visit your PC. system administrator. Much more attractive is the option of revealing the administrator’s password, logging into Windows using its password, making the necessary changes or removing the necessary information accessible only to the computer administrator, and safely logging out of the system without traces of your visit. Elcomsoft System Recovery Professional does an excellent job of these and many other functions related to administrator and user accounts. Using it, you can find out the administrator password for Windows 7, XP, 2000, Server 2003 and 2008. The program is paid, but it is not difficult to find its “specific” version on the Internet. Let's take a step-by-step look at how you can find out Windows password with its help, as well as its other capabilities.
Removing Windows password - Elcomsoft System Recovery Professional
Removing the Windows password in the following way. After spending some time searching for an image of the Elcomsoft System Recovery Professional program, we downloaded it and burned it to disk. Next, we configure the BIOS to boot from the drive and, after booting from the disk, we get the first window. Select the desired language, agree to the license terms and move forward "ok"
Here, most likely, in most cases there is no need to do anything and we continue to move “Next”. 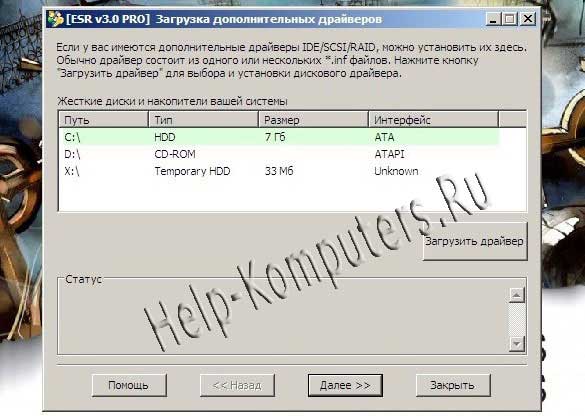
Since our goal is to find out the Windows password, here we leave everything unchanged and move on to the next point. 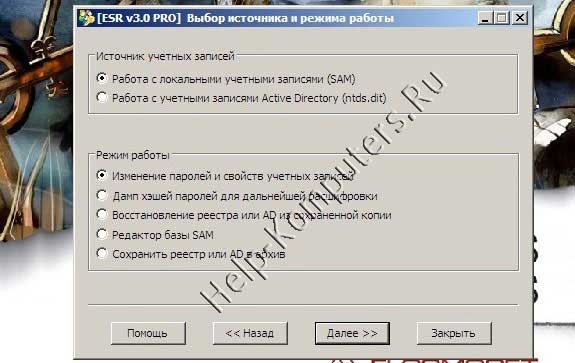
At this stage we are asked to select the Windows directory of the system with which we are working. If there are several operating systems installed on the computer in different logical partitions or on one, then we need to know which one applies to our system (Windows, Windows 0, etc.). But in most cases, one operating system is installed, so there will be no choice. We leave the default settings and move on to the most interesting part. 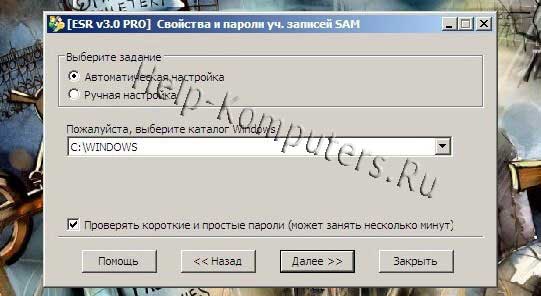
After the program works for a short time to determine passwords, statuses and other attributes of accounts, the program will give us a window with the passwords of all users and administrators of the Windows operating system under study. Here we can rewrite all the passwords of interest and exit the program - “Close”. However, if we want to work with any account, we need to select it and click “Next”, moving to the next window for editing account parameters. 
This window shows what actions we can take to change the settings and password of the administrator (user) account: changing the password, raising the account privilege to admin status, unlocking accounts that have the status "disabled" or "locked". The program supports any file systems, defines passwords written in all languages that are localized in OS Windows. Using the program you can find out the administrator password on Windows 7, NT 4.0, Windows Vista, 2003 Server, 2000, XP and Windows 2008 Server. 
Agreeing with possible problems we get the last window before restarting the computer. 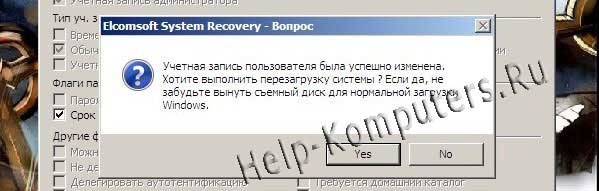
If, at the stage of viewing all passwords, you click “Close”, you will receive the following window. If we are only talking about finding out the Windows password, it is advisable not to risk possible problems, but to calmly log in with the revealed admin password and make all the necessary changes to the accounts from under the system. Well, if we are talking about unlocking an account or its password has expired, then nothing can be done about it. 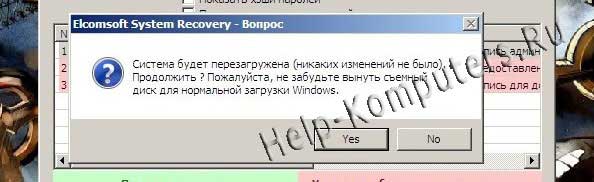
Changing the password of any Windows user using ERD Commander
This video tutorial shows how to use boot disk ERD Commander 2007 can change the password of any Windows user, including the administrator.
If you still fail to change the administrator password, you can always call a computer service technician to unlock your computer.
Was the material useful? Click the button -
If you have no idea where the “Windows system folder” is located and you have little practical knowledge of the computer, then you will need a special program SAMInside and LiveCD. In order to find out the Windows administrator password, you can find out in detail on the website http://mycompplus.ru/-windows/47-windows-7/325-pass-admin.html, there you can remove the password without additional programs.
A special disk on which the OS is recorded, in which it can work and run without any installation on HDD personal computer, use the LiveCD program. Based on various operating systems there is a large number of different LiveCDs. You can choose an image that is based on any Windows edition and Linux, that is, ready-made assemblies. You need to burn the downloaded image to disk to use the computer boot. When running Windows system, access to such a file is completely impossible, so this is necessary because , where “Hashes” of passwords are stored and protected by the operating system.
First, you need to write the SAMInside program to a flash drive, downloaded in advance, and insert the flash drive before starting the LiveCD.
You will need SAM, after booting from the LiveCD, it is located in the system Windows folder: “Windows\System32\Config\. This file stores password “hashes” for administrators and all Windows users.
The second step is to launch special program SAMInside, and you will need a second computer with a ready-made operating system Windows, where you need to copy special file SAM, and then run the program. Using the guessing method, the SAMInside program selects the password of all possible variants, and if the password is long and complex, this selection may take a long period of time.
You will most likely not be able to find out the Windows administrator password if your personal computer If the boot function from flash drives and disks is disabled, then the network has no options, remove the hard drive or enable boot from the computer to copy the SAM file itself. In the Windows operating system there is a built-in user “Administrator”, which is without a password, and can be accessed when starting in safe mode, by default, or by pressing the “F8” button, only before the operating system starts loading. You will be able to change and log in the password of any user if it has not been disabled on your computer, that is, it is impossible to find out, only reset or change.
If you do not have the most necessary skills in working with a computer, then you should not even engage in this process yourself.
I'll start in order:
1. You need to boot from Live CD or Live USB
2. Take files SAM And system
3. Find out the password from hashes from files SAM And system
1. If there is no BIOS password or/and you can boot from external media, then proceed to paragraph 2. But if there is a BIOS password, then you can try to break it, there are several ways:
A) Jumpers and battery on the motherboard
Locate the BIOS jumper on the computer motherboard. This jumper is often called CLEAR, Clear CMOS, JCMOS1, CLR, CLRPWD, PASSWORD, PASS or P.S.W., as shown in the figure on the right. You will need to move the jumper from its position. For example, in the picture on the right, the jumper shorts pins 1 and 2, you just need to move it so that it shorts pins 2 and 3. Once the jumper is moved, turn on the computer and the password should be cleared. Once the password is reset, turn off the computer and return the jumper to its original position. The location of the jumpers is determined by the computer and motherboard manufacturers. However, below are some general thoughts on where to find it. Remember that most motherboards have dozens of different jumpers, make sure you change the CMOS jumper and not something else. If these general guidelines do not help you find the jumper relative to your motherboard, then try using the documentation on your computer or follow the instructions below.
1. On the edge of the board - Most jumpers are located on the edge of the motherboard for easy access. Inspect all visible edges of the motherboard.
2. Near the CMOS Battery - Some manufacturers choose to place jumpers near the CMOS battery.
3. Near the processor - some manufacturers choose places for jumpers near the computer's processor chip.
4. Under the keyboard or on the bottom of the laptop – If you are working on a laptop, the switch is located under the keyboard or on the bottom of the laptop in the compartment where the RAM(in new laptops, only the settings are disrupted by a jumper! The approximate year of release of “new” laptops is 2004, that is, now there are almost no old ones).
5. Other Locations - While it is possible that the jumper may not be in a visible location, most manufacturers try to make life easier by placing the jumper in any other visible, easily accessible location, look carefully.
Removing the CMOS battery, which is shown in the figure on the right, will reset all CMOS settings, including the password. To do this, locate and remove the CMOS battery from the motherboard for at least five minutes. After that, put the battery back into the computer and turn it on again.
But in laptops and netbooks, it is IMPOSSIBLE to reset the password in this way, since there is energy-saving memory - eeprom!
For owners of laptops and netbooks, only the method is suitable b
b) If, when you enter the wrong password three times, a window with numbers pops up, you need to write them down on a piece of paper and write them here, and I will tell you the BIOS password. So, when we were able to boot from external drives (cd/dvd, usb), we proceed to the point 2
2. Need to get out of installed windows(partition of the disk on which the OS is located and from which you need to find out the password) files SAM And system. We come in any way file manager drive letter(usually WITH):\WINDOWS\system32\config we throw the files into a place convenient for you, for example on a flash drive SAM And system After we have password hashes ( SAM, system), let's start 3rd point
3. Run the program saminside, it can be found in the section “File directory” Click File - import registry files SAM And system... Select the files that were pulled out first SAM, Then system Now we choose how the program will break (by brute force, using tables, using a mask or dictionaries), in the “Audit” tab. We go to the service settings and select the tab corresponding to the attack and configure, for example, the tab, Brute force attack: The first checkbox, “All printable characters with ASCII codes 32...255” means that the program will select passwords consisting of characters (brackets , “dog”, dot…, Russian and English alphabet, including spaces). If the password is not small, then it will take a very long time to break in this way, it is better to select the following checkboxes, in which only the English alphabet in capital letters, the next checkbox is only the English alphabet in small letters. Further only numbers; symbols, and the last parameter of symbols are those that you enter in the box (without commas, for example, ytsuken12346;%?**)qwr) Generating passwords Here it is advisable to choose the most approximate password value - from how many to how many. If the password is very big then.
