Passwords are the keys to your virtual data storages on the Internet - from your mail account, Online Games, personal page on social networks, etc. Of course, it must 100% meet such criteria as reliability. That is, it must be resistant to burglary, or selection. Unfortunately, many users ignore this simple but mandatory requirement for passwords. And as a result, as a rule, they become victims of intruders. They lose money, confidential data, gameplay achievements, etc.
It is known that 1% of Internet users, either because of laziness or because of negligence when registering, prefer to use primitive combinations that can be picked up in 3-4 attempts. Examples are "123456", "qwerty", "mypassword". This is certainly very stupid. A "light" key for the user is also "light" for the attacker.

This article will tell you how to create strong passwords and how to test them for hacking resistance.
What is a secure password?
Good keys from account have the following characteristics:
1. The length is not less than 10-15 characters (the most stable combinations are even more - 20-35 characters).
2. Symbols: large and small English letters, numbers, special characters.
3. The combination lacks dictionary words (parol, kod, vhod), personal data (phone number, name, e-mail, etc.), logical sequences of letters and numbers (1234, 246810, abcdefg).
The more complex and reliable the combination, the more difficult it is to make its selection. It can take over 1.5 million years to establish a user-created sequence of 12 characters.

Complex key creation
Ordinary Internet users and security experts have already found many correct answers-solutions to the question "How to create a strong password?" Throughout this article, we'll walk you through three of the most practical ways.
Method number 1: substitution of letters
Not at all first mobile phones the Russian language was supported, and their owners sent SMS using transliteration. That is, they wrote in Latin letters in Russian, and the missing letters were replaced with symbols. For example: "h" - "4". The phrase "What are you doing?" Looked like "4to delaesh?" The same principle underlies this method composing keys.

Take a word or phrase, and then write it down using "tricky" notation. Instead of spaces, you can use any special characters "~", "/", "." As separators. etc. For example, you can come up with the following combination:
Let's write the "danger zone" as "onACHA9I # 3OHA".
As you can see, we wrote down the words in Latin letters and, in addition, replaced some Russian letters. Instead of "n" - "n", "i" - "9I", "z" - "3" (digit "three"). And put a separator "#" between the words. So it turned out to be a rather complicated option. To unravel this type of symbolic combination, computer villains will have to do their best.
To help, a table of symbolic designations of Russian letters:
Method number 2: creating a "readable" key in the generator
1. Open the online service in your browser - http://genpas.peter23.com/.
2. In the "Operating mode" option, click the "Spoken password ..." radio button.
3. Additionally enable / disable character sets for key combinations and set its length.
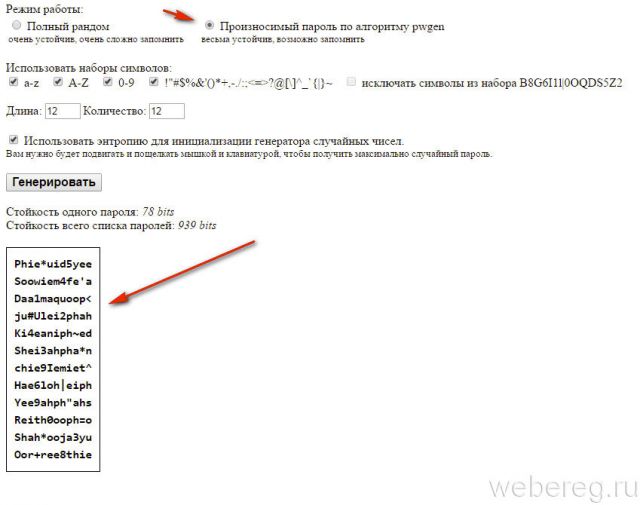
4. Click the Generate button.
5. Choose the most the best option from generated sequences.
6. Break the selected password into fragments of 2-3 characters and give each fragment a certain meaning. In such a "logical chain" it is very easy to remember the most difficult combination. As an example, let's take a look at the key generated in this generator:
Xoh) ohfo1koh
- Xoh) - can be read as "Hoh" + "smiley";
- oh - "oh";
- fo1 - let it be some kind of mysterious abbreviation;
- koh - koh - again a variation of the initial syllable.
Method number 3: adding special characters to simple words
1. Take as a basis any word you know well:
space2017
2. Come up with a combination of special characters of 2 or 3 characters.
«+_&»
3. Add a combination at the beginning and at the end of the word in the mirror image.
+ _ & space2017 & _ +
4. As a result, you will receive a sufficiently "strong" key. Of course, it cannot be called the most stable, but it is easy to remember and is not primitive in structure.
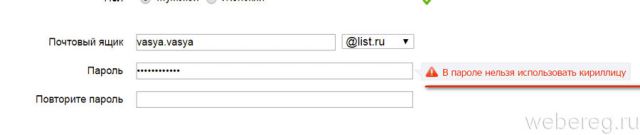
Attention! Before creating a password, be sure to read the requirements of the service you are registering with. For example, the Cyrillic alphabet (Russian letters) cannot be used on the Mail.ru portal.
Checking the key for reliability
You can analyze the stability of the selected combination on special services.
Provides the user with a detailed analysis of the specified combination (character sets, length), and also estimates its complexity in percent.
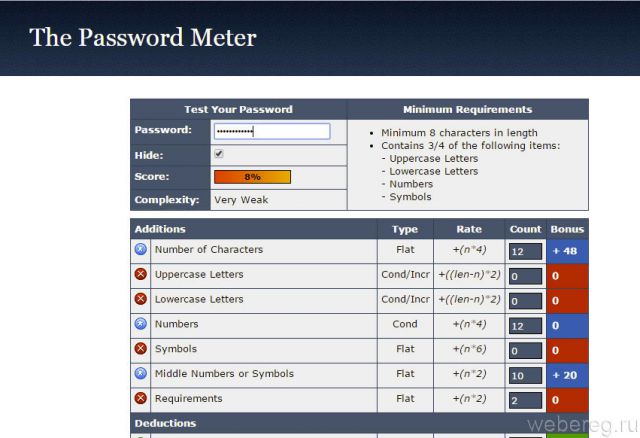
Reports how long it will take to find the specified key. Warns about invalid (primitive) character sequences.

Use only strong passwords! They are the key to your online safety.
Password checking is necessary when you are not sure or doubt its complexity and sufficient security. Fortunately, for this there are online services that allow you to check how secure a particular password is. More on this.
Why check password strength?
In fact, checking a password for strength is primarily necessary for those who do not know what passwords should be. The article gave advice on creating complex, practically uncrackable passwords. The 3 online services discussed in this article will help you create such a password.
How do I check the complexity of a password?
There are online services that allow you to check the complexity of the password, as well as how long it takes for attackers to guess it. Today we will consider 3 such services that deserve the most attention.
Service number 1.
This service, as you may have guessed, is probably from Kaspersky Lab, it is called - "Save the world with a word." This service helps to create strong passwords by checking them for complexity.
The service shows that given password hacked in 1 second. So it is, even with the help of brute force (a program for guessing passwords) this password will be bruised faster than you say "Oops!"
And here is a more complex password using numbers, and letters of different case:
Such a password will be very difficult to guess; in general, the password is reliable and to some extent uncrackable (unbreakable).
As you can see, the service shows how long it takes to crack this or that password on different computers, these are ZX Spectrum (80s), Mac Book Pro (2012), Tianhe-2 (a supercomputer developed in China), and also using a network of computers (botnet).
Service number 2.
The next service for checking password strength from Microsoft. It is located at this address.
Everything is simple here, we enter the required password and the program shows how reliable it is. Nothing extra. The degree of reliability is indicated by the 4 rectangles below. One rectangle is a very simple password, and four green rectangles are a complex password.
Service number 3.
The third and final service for checking password complexity today. The site is called “How secure is my password? ".
The interface is in English, but that's okay. In the line "Password" you must enter a password and the service will also show how secure it is, this is your password.
In the example above, the service indicates that the password is good (this is indicated by the green background of the site). If the background of the site is red, then the password is also not strong.
Below you can still see the approximate time required for a rough selection (brute force). And also, if the password you entered is not complex and secure, then the service will indicate this and give advice on creating a more secure password.
Of course, there are no uncrackable passwords, these services only show how much a picker will have to crack (using brute force). But after all, there are other ways of hacking - social engineering, the use of keyloggers without the knowledge of the PC user, and so on. Therefore, keep your passwords wisely and do not give them to anyone.
Many sites try to help users install more complex passwords... For this, basic rules are established, which usually require at least one uppercase letter, one lowercase letter, one digit and so on. The rules are usually primitive like this:
"password" => ["required", "confirmed", "min: 8", "regex: / ^ (? = \ S *) (? = \ S *) (? = \ S * [\ d]) \ S * $ / ",];
Unfortunately, such simple rules means that the Abcd1234 password will be considered good and of good quality, just like Password1. On the other hand, the mu-icac-of-jaz-doad password will not be validated.
Here are the first two passwords.

And here are two passwords that will not pass the strength test.


What to do? Maybe you shouldn't force the use of special characters and introduce all the new rules, such as prohibiting the repetition of several characters in a row, using not one, but two or three special characters and numbers, increasing the minimum password length, etc.
Instead of all this, it suffices to do simple thing- easy to install minimum entropy constraint password, and that's it! You can use the ready-made evaluator zxcvbn for this.
There are other solutions besides zxcvbn. Just last week, at the ACM Computer and Communications Security conference, a scientific paper (pdf) by security experts from Symantec Research and the French research institute Eurecom was presented. They developed new program for password strength testing, which estimates the approximate number of brute-force attempts required using the Monte Carlo method. The proposed method differs in that it requires a minimum amount of computing resources on the server, is suitable for a large number probabilistic models and at the same time quite accurate. The method was tested on passwords from the Xato database of 10 million passwords, which are in the public domain (copy on Archive.org) - he showed good result... True, this study by Symantec Research and Eurecom is more of a theoretical nature, at least they did not publish their program in open access in any acceptable form. Nevertheless, the meaning of the work is clear: instead of heuristic rules for checking passwords, it is advisable for websites to implement an entropy check.
