Program FileControl designed to control access to various ports and external devices on local network computers ( USB, CD/DVD, disk drives, printers, etc.), as well as Wi-Fi and Bluetooth interfaces. Used to provide information security in office local networks.
It is known that the greatest danger to the security of local networks is not external threats (from the Internet), but internal ones. Insider threats are caused by office workers having access to important information from the inside - from their computers connected to a local network. If this access is not controlled, the consequence may be unauthorized copying and deletion. confidential information, as well as appearance on work computers malware(viruses, Trojans) and simply useless files (for example, videos and music). External sources have recently posed a particular danger to the information security of organizations. USB devices, due to their prevalence, large capacity and ease of connection to office computers.
Why do you need FileControl?
Program copes effectively with the above problems in office local networks, limiting the use various devices according to the rules established by the administrator, and saving information about operations with files on these devices. FileControl provides effective protection against internal threats - information leaks, destruction of valuable information, insiders, USB viruses and others. The target audience FileContro l - local network administrators, executives and managers at various levels, security officers.
Features, principles of operation and device FileControl
Basic FileControl Functions - displaying devices connected to the computer, allowing/prohibiting work with various of them and recording operations with files on these devices. Monitors user actions special driver tracking, which is installed on each computer remotely from the server.
FileControl Features
Access control:
FileControl controls following devices and ports:
USB port and all devices connected via USB(flash drives, external hard disks, cameras, Cell Phones, PDAs, mp3 players, etc.), and USB printers and all USB types disks;
optical CDs and DVD drives, FDD 3.5″ drives;
external I/O ports - COM, LPT, IrDA;
Bluetooth and Wi-Fi interfaces.
Access control is carried out both for computers and for individual Windows users. For devices to which access must always be allowed (USB keys, scanners, printers, etc.), a white list has been implemented.
Monitoring and statistics
FileControl shows USB devices connected to computers and keeps a log of user activity from external drives information. Information about the time of connection/disconnection of devices and which files were read or written and when is saved in the database. By using convenient system Search with filters to quickly find the data you need. It is also possible to export this data to MS Excel.
File shadow copying
Without the knowledge of users, the program saves all files that were read from or written to external USB drives into a separate folder on the server.
Easy to install and use
All program modules are contained in one distribution kit, which is installed on the server in automatic mode. After this, you need to select local network computers to install tracking drivers on them. This is done remotely - you can select one by one by specifying a name or IP address, or several at once by specifying a range of IP addresses, or by importing from Active Directory. Also possible manual installation tracking drivers.
The structure and principles of operation of FileControl
FileControl consists of four modules- they are all contained in one distribution:
Server
It is a service that constantly exchanges information with tracking drivers. Installed on an office local network server, it allows/prohibits certain actions, saves information in a database. Managed using the administration console.
Custom
This is a tracking driver that controls access directly on client computers and collects information about devices and files. Tracking drivers are installed on local network computers remotely, through the administration console. Manual installation on each computer is also possible.
Administrative
Control panel from which the server is managed FileControl, installation and removal of tracking drivers, as well as working with the database.
Database
FileControl has an integrated SQLite database. It stores all information about computers, devices, files, and access rules. Queries to the database are made through the administration console.
The only way to completely control operations with files on external devices is to install a driver on all computers on the local network that is invisible to computer users. Tracking driver FileControl- low-level, working at the OS kernel level. It monitors all write or read operations to removable devices. When attempting to write or read to a device, the tracking driver checks access rights and acts in accordance with them, i.e. allows or denies an action. At the same moment, information about the action taken is sent to the server. The tracking driver receives access level settings from the server when the client computer boots, or when they are changed by the administrator.
FileControl server side- a service that is installed on the server. This module is used to collect data from tracking drivers and send them access rights settings. The service saves the collected data about users, their devices, and the work with files on these devices in the SQLite database.
Control Panel FIleControl - This is the user interface of the program. Serves to monitor connected USB devices, changing access rights for users, remote installation of tracking drivers and database searches. It is an exe application that can be launched from any computer on the local network, and not just on the server.
Instructions for setting up and using FileControl 2.0
FileControl consists of three modules - administrator (program control panel), user, also called the tracking driver, and server. The computer on which you have now installed the program serves to FileControl server. A service was installed on it, the function of which is to collect information from tracking drivers on local network computers and allow or prohibit certain actions on these computers, as well as record information about events on these computers in a database.
After installing the server, you need to install FileControl tracking drivers on local network computers, which will control access to external devices and ports in accordance with the rules you set, receive and send information to the server. If there is no connection with the server, the driver will continue to work according to the rules established before the connection was lost.
The program is managed through the Control Panel FileContro l, which communicates with the server and serves to manage access rights on local network computers, as well as to view information from the database. The control panel is installed with the server, but can also be launched from any computer on the local network.
Preliminary firewall settings(firewall)
Attention! For the FileControl server part to work correctly, the following ports must be opened on the server: TCP protocol: 4010, 4011, 4003.
Port assignment:
4010 and 4011 - for connecting the administrative module (control panel) and tracking drivers to the server FileControl;
4003 - for shadow copying of files.
Before you begin, make sure that your firewall on the server (that is, on the computer where the program was just installed) does not block these connections.
Login to the program
Management is carried out through the administrator module - Panel FileControl controls(file `fcadmin.exe`, located in the folder where the program is installed), which can be launched from any machine on the local network. When entering the program you need to specify the address or name of the server FileControl. The default login password for the administrator module is not set. If necessary, you can specify it in the “Settings” section after opening the program.
After entering the program, we begin to configure it.
Add a computer and install the tracking driver
FileControl allows you to install tracking drivers on computers on your local network in two ways - remotely or manually. Remote installation is a standard operating mode that allows you to quickly install drivers on any number of computers directly from the FileControl Control Panel. If your the local network is configured correctly and you have domain administrator rights (for a network built on a domain), or local administrator rights on remote computers (for a network without a domain), then remote installation will work correctly. In other cases, tracking drivers will have to be installed manually by running a special FileControl driver installer on each computer.
Remote installation of tracking driver
Information about the program's actions is displayed in the corresponding window. If the installation of the tracking driver was completed correctly, it starts working without restarting the computer.
Click on the “Add computers” button. The dialog box that opens contains a list of computers selected for driver installation and buttons for adding computers to this list different ways. Computers can be added to the list one by one, by specifying the address or name of an individual computer, or en masse, by specifying a range of IP addresses, or by importing them from the Windows AD domain. Using last method you need to specify the login and password of any user who is allowed access via LDAP. Or, if the security policy allows only the administrator to access via LDAP, then enter the information of the Active Directory domain administrator.
Add computers to the list with one of ways in the list We check the boxes for which we need to install the driver and click the “Install >>” button. If required, enter the administrator login and password on the remote machine. To add from Active Directory, you must specify the domain administrator login and password
The installation may take some time - please wait for it to complete. Information about the program's actions is displayed in the corresponding window. If the installation of the tracking driver was completed correctly, it starts working without restarting the computer.
Possible problems and solutions
If during installation you encounter problems accessing remote computer, then you need to check the accessibility by typing in address bar`\computeradmin$`, where computer is the name or IP address of the remote computer.
At USB connection A flash drive or any other USB device to your computer creates a set of files with which you can access them. When you work in file manager everything is simple enough, but once it comes to the console everything becomes much more difficult.
It is important for every beginner to be able to identify connected devices, be it usb flash drives, SD cards or hard drives so as not to write something to the wrong place or format the wrong disk. In this article we will look at several ways to view usb devices Linux connected to a computer.
List of connected Linux devices
IN operating system Linux uses a special management philosophy. All objects, including devices, are considered files. When a device is connected to the system, a file is created for it in the /dev/ directory.
Usually, after you connect any USB flash drive or other storage device to a system with desktop environment installed, the device is automatically mounted in the /media/username/device_label/ folder, and then you can access the files from the device in this folder. However, there are situations when you need to manually mount the USB and then this option will not help.
All device files are located in the /dev/ directory. Here you can find the sda, hda files, which are HDD, as well as sda1 or hda1 files, which allow you to access disk partitions. We have already discussed all this in detail in the article. You can see a list of all devices in the /dev/ directory using the command:
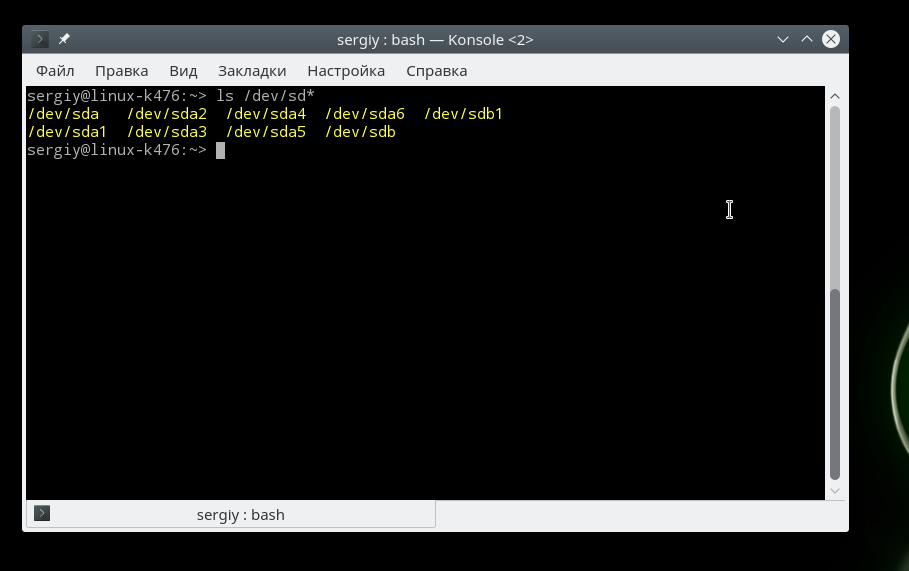
Now it remains to understand which of these device files belong to USB devices and which devices exactly.
How to view Linux USB devices
To find out more detailed information about each device connected to your system and see the list of linux devices, you can use the df command. It is used to view free space on disk:
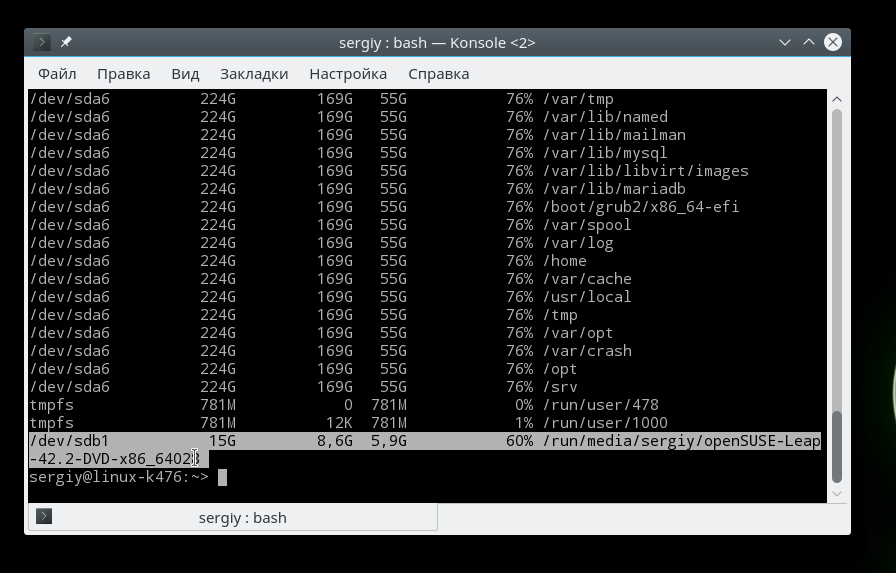
By the total size and occupied space, you can determine which device is your flash drive, but this way to view Linux devices is not very convenient and it only works with an already mounted flash drive; there are several more that provide more accurate information.
The lsblk command displays a list of all block devices connected to your computer. The utility displays not only their size, but also their type (disk/partition) as well as the major and minor device numbers. Here it’s a little easier to find a flash drive, we see two disks, and if the first with a size of 698 gigabytes is a hard drive, then the second is exactly a flash drive:
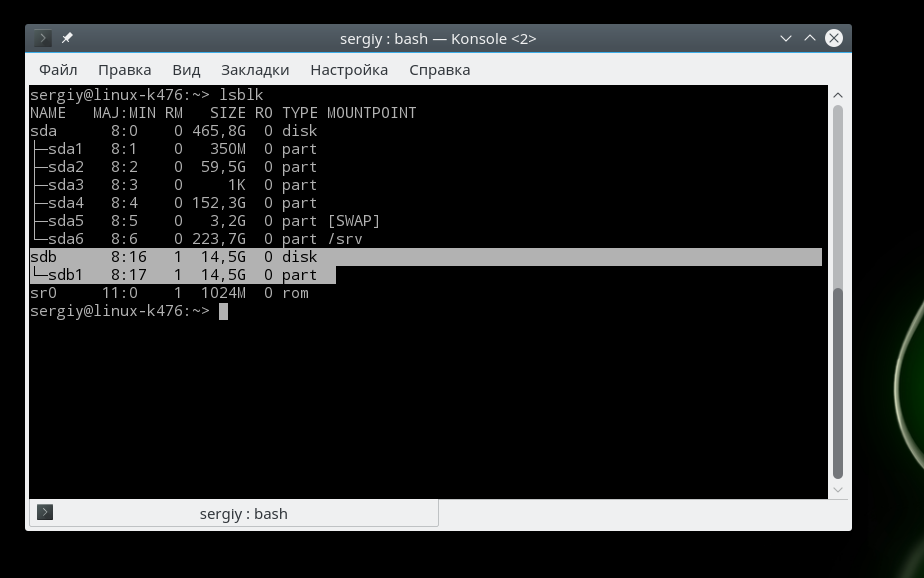
There is another way, this is the fdisk utility. It allows you to view the partition table on all block devices connected to the computer. But the utility must be executed as a superuser:
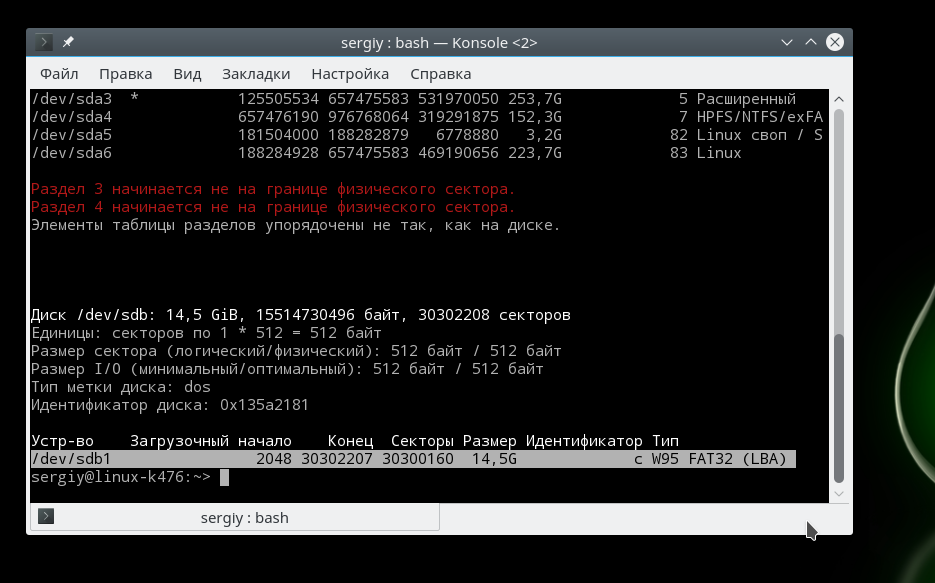
You can also find out about the connected USB device by looking at the kernel message queue dmesg. Information about all operations that occur in the kernel is stored here. The name of the flash drive just connected to the computer will be displayed here. To view kernel messages, run:
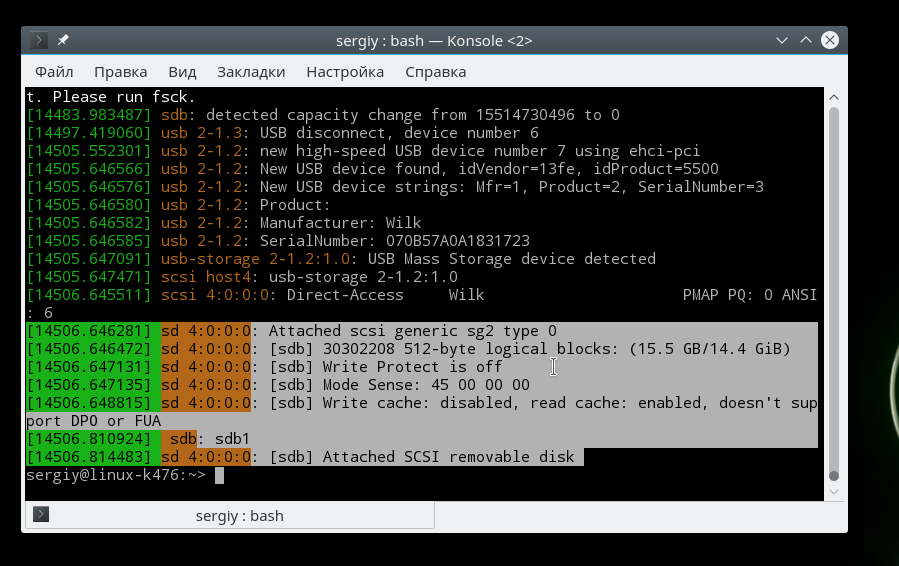
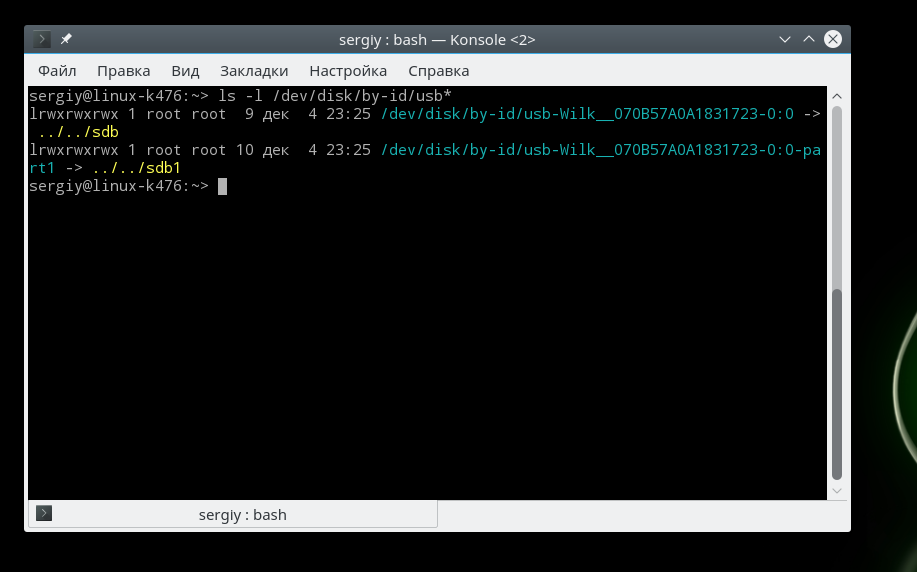
To see which of the sd devices are USB, use the following command:
ls -l /dev/disk/by-id/usb*
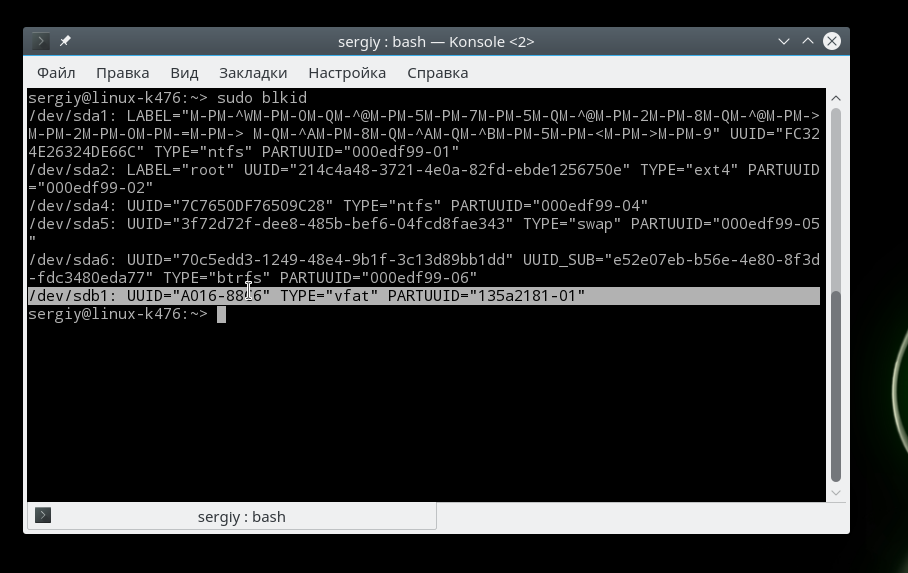
You can try to identify your flash drive in the system through the terminal using the blkid utility. It displays the UUID identifiers of all connected devices, as well as the file system:
conclusions
In this article, we looked at how to view Linux usb devices, as well as how to find out the name of your usb flash drive in the system. You can use any of the commands that you like, or several at once. But now you know how to accurately determine the file name of your flash drive.
How many in modern world There are USB devices that we connect to our computer every now and then. Some we use every day, some are constantly connected, and some come to us and leave forever. Did you know that your good iron friend remembers all this data and carefully stores all this information in his memory? This is done so that if such a device is reused, the computer does not have to look for information about it again and install its driver. If you constantly connect some devices, this is certainly very convenient, since you don’t have to install them again each time. But what if you never connect some of the devices again? For such cases there is special program called USBDeview, which will help you remove from your computer all unnecessary entries about USB devices that you no longer use.
The principle of working with USBDeview is very simple. The program displays all devices ever connected via USB ports; all you have to do is select those that you will definitely never connect again, select them and delete them. Everything is very simple.
USBDeview in its list displays enough detailed information about a particular USB device, so you can easily find and delete records about long-unused pieces of hardware. The easiest way to find such devices is to look and compare the list of dates last connection. Let’s say that among all the available devices there are five that were connected more than six months ago. Such devices can be safely removed.
Another way to select candidates for deletion is by device names. If you suddenly see in the list the name of a phone that was sold a long time ago, or a device that was replaced by another (as a result of a breakdown or for any other reason), then entries about such elements can also be safely deleted from the system, because they are absolutely not needed there.
Such a tool is very useful for cleaning the system and can be useful to any user. USBDeview works without installation and has a Russian interface (if you download the crack). The size of the program is very modest, so it should not be one of the first candidates for deletion to free up useful disk space.
