Express wired Internet is becoming more and more accessible. And along with the development of mobile technology, the issue of using home internet on each device. A Wi-Fi router serves this purpose; its purpose is to distribute wireless connection Internet between different users.
Special attention should be paid to the security of your network.
When purchasing, you just need to configure it the first time you turn it on. A disk with a configuration utility is supplied with the router. Use it to configure home network as easy as pie. But, nevertheless, inexperienced users often have problems at the stage of network security settings. The system prompts you to select an authentication method, and there are at least four options to choose from. Each of them has certain advantages and disadvantages, and if you want to protect yourself from the actions of attackers, you should choose the most reliable option. This is what our article is about.
Authentication Methods
Most home router models support the following network authentication methods: no encryption, WEP, WPA/WPA2-Enterprise, WPA/WPA2-Personal (WPA/WPA2-PSK). The last three also have several encryption algorithms. Let's take a closer look.
Lack of protection
This method speaks for itself. The connection is completely open, absolutely anyone can connect to it. This method is usually used in public places, but it is better not to use it at home. The minimum that this threatens you with is that your neighbors will occupy your channel when connected, and you simply will not be able to receive maximum speed according to your tariff plan. In the worst case, attackers can use this for their own purposes, stealing your confidential information or committing other illegal actions. But you don’t need to remember the password, but you must admit, this is a rather dubious advantage.

WEP
When using this network authentication method, the transmitted information is protected using a secret key. The type of protection is " Open system" and "Shared Key". In the first case, identification occurs through filtering by MAC address without using an additional key. The protection is, in fact, the most minimal, and therefore unsafe. In the second you have to come up with secret code, which will be used as the security key. It can be 64, 128 of 152 bit. The system will tell you how long the code should be, depending on its encoding - hexadecimal or ASCII. You can set several such codes. The reliability of protection is relative and has long been considered outdated.

WPA/WPA2 – Enterprise and WPA/WPA2-Personal
A very reliable method of verifying network authenticity, in the first case it is used in enterprises, in the second - at home and in small offices. The difference between them is that in home version a permanent key is used, which is configured at the access point. Together with the encryption algorithm and the connection SSID, it forms a secure connection. To gain access to such a network, you need to know the password. Therefore, if it is reliable and you do not disclose it to anyone, this is an ideal option for an apartment or house. In addition, almost all manufacturers mark it as recommended.

In the second case, a dynamic key is used and each user is assigned an individual one. There is no point in bothering with this at home, so it is used only in large enterprises where the security of corporate data is very important.
Additional reliability also depends on the encryption algorithm. There are two of them: AES and TKIP. It's better to use the first one, since the latter is a derivative of WEP and has proven to be a failure.
WPA And WPA2 (Wi-Fi Protected Access) - represents an updated device certification program wireless communication. It is assumed that WPA will replace the widespread security technology for wireless networks. An important characteristic is compatibility between many wireless devices, both at the hardware and software levels. On this moment WPA and WPA2 are developed and promoted by the Wi-Fi Alliance.
Basic Concepts
WPA provides support for 802.1X standards, as well as the EAP (Extensible Authentication Protocol) protocol. It is worth noting that WPA supports encryption in accordance with the AES standard (Advanced Encryption Standard), which has a number of advantages over that used in WEP
A big advantage when implementing WPA is the ability of the technology to work on an existing hardware, and is intended to replace WPA. It implements CCMP and encryption of Wi-Fi devices.
Vulnerability
On November 6, 2008, at the PacSec conference, a method was presented that allows one to crack a key. This method allows you to read the data transmitted from the access point to the client machine, as well as transmit fake information to the client machine. The data transmitted from the client to the router has not yet been read. It is also said that WPA2 is not susceptible to this attack.
Links
See what "WPA2" is in other dictionaries:
WPA2- (Wi Fi Protected Access 2 Acceso Protegido Wi Fi 2) es un sistema para proteger las redes inalámbricas (Wi Fi); creado para corregir las vulnerabilidades detectadas en WPA WPA2 está basada en el nuevo estándar 802.11i. WPA, por ser una versión… … Wikipedia Español
WPA2
WPA2- Wi-Fi Protected Access 2 (WPA2) ist die Implementierung eines Sicherheitsstandards für Funknetzwerke nach den WLAN Standards IEEE 802.11a, b, g und n und basiert auf dem Advanced Encryption Standard (AES). Er stellt den Nachfolger von WPA dar,… … Deutsch Wikipedia
Wi-Fi Protected Access
WPA-PSK- Wi Fi Protected Access Wi Fi Protected Access (WPA et WPA2) est un mécanisme pour sécuriser les réseaux sans fil de type Wi Fi. Il a été créé en réponse aux nombreuses et sévères faiblesses que des chercheurs ont trouvées dans le mécanisme… … Wikipédia en Français
Wi-Fi protected access- (WPA et WPA2) est un mécanisme pour sécuriser les réseaux sans fil de type Wi Fi. Il a été créé en réponse aux nombreuses et sévères faiblesses que des chercheurs ont trouvées dans le mécanisme précédent, le WEP. WPA respecte la majorité de la… … Wikipédia en Français
Wi-fi protected access- (WPA et WPA2) est un mécanisme pour sécuriser les réseaux sans fil de type Wi Fi. Il a été créé en réponse aux nombreuses et sévères faiblesses que des chercheurs ont trouvées dans le mécanisme précédent, le WEP. WPA respecte la majorité de la… … Wikipédia en Français
Robust Secure Network- Wi Fi Protected Access 2 (WPA2) ist die Implementierung eines Sicherheitsstandards für Funknetzwerke nach den WLAN Standards IEEE 802.11a, b, g, n und basiert auf dem Advanced Encryption Standard (AES). Er stellt den Nachfolger von WPA dar, das… … Deutsch Wikipedia
Wi-Fi Protected Access 2- (WPA2) ist die Implementierung eines Sicherheitsstandards für Funknetzwerke nach den WLAN Standards IEEE 802.11a, b, g, n und basiert auf dem Advanced Encryption Standard (AES). Er stellt den Nachfolger von WPA dar, das wiederum auf dem… … Deutsch Wikipedia
Wireless security- An example wireless router, that can implement wireless security features Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. Many laptop computers have wireless cards pre installed. The... ... Wikipedia
The question often arises: what type of Wi-Fi encryption to choose for your home router. It might seem like a small thing, but if the parameters are incorrect, problems may arise with the network, and even with the transfer of information via an Ethernet cable.
Therefore, here we will look at what types of data encryption are supported by modern WiFi routers, and how the aes encryption type differs from the popular wpa and wpa2.
Wireless network encryption type: how to choose a security method?
So, there are 3 types of encryption in total:
- 1. WEP encryption
The WEP encryption type appeared back in the 90s and was the first option for protecting Wi-Fi networks: it was positioned as an analogue of encryption in wired networks and used the RC4 cipher. There were three common encryption algorithms for transmitted data - Neesus, Apple and MD5 - but each of them did not provide the required level of security. In 2004, IEEE declared the standard obsolete due to the fact that it finally ceased to provide secure network connections. At the moment, it is not recommended to use this type of encryption for wifi, because... it is not crypto-proof.
- 2.WPS is a standard that does not provide for the use of . To connect to the router, simply click on the appropriate button, which we described in detail in the article.
Theoretically, WPS allows you to connect to an access point using an eight-digit code, but in practice, only four are often enough.
This fact is easily taken advantage of by numerous hackers who quickly (in 3 - 15 hours) hack wifi networks, so use this connection also not recommended.
- 3.Encryption type WPA/WPA2
Things are much better with WPA encryption. Instead of the vulnerable RC4 cipher, AES encryption is used here, where the password length is arbitrary (8 - 63 bits). This type encryption provides a normal level of security, and is quite suitable for simple wifi routers. There are two types of it:
Type PSK (Pre-Shared Key) – connection to the access point is carried out using a pre-defined password.
- Enterprise – the password for each node is generated automatically and checked on RADIUS servers.
The WPA2 encryption type is a continuation of WPA with security improvements. This protocol uses RSN, which is based on AES encryption.
Like WPA encryption, WPA2 has two modes of operation: PSK and Enterprise.
Since 2006, the WPA2 encryption type has been supported by all Wi-Fi equipment, and the corresponding geo can be selected for any router.
Advantages of WPA2 encryption over WPA:
Encryption keys are generated during the connection to the router (instead of static ones);
- Using the Michael algorithm to control the integrity of transmitted messages
- Using an initialization vector of significantly greater length.
In addition, you should choose the type of Wi-Fi encryption depending on where your router is used:
WEP, TKIP and CKIP encryption should not be used at all;
For a home access point, WPA/WPA2 PSK is quite suitable;
For this you should choose WPA/WPA2 Enterprise.
With the spread of wireless networks, the WPA and WPA2 encryption protocols have become known to almost all owners of devices connecting to Wi-Fi. They are indicated in the connection properties, and the attention of most users who are not system administrators, attract a minimum. It is quite enough to know that WPA2 is an evolution of WPA, and therefore WPA2 is newer and more suitable for modern networks.
Definition
WPA is an encryption protocol designed to protect wireless networks of the IEEE 802.11 standard, developed by the Wi-Fi Alliance in 2003 as a replacement for the outdated and insecure WEP protocol.
WPA2- an encryption protocol that is an improved development of WPA, introduced in 2004 by the Wi-Fi Alliance.
Comparison
Finding the difference between WPA and WPA2 is not relevant for most users, since all the protection wireless network comes down to a choice more or less complex password for access. Today the situation is such that all devices operating in Wi-Fi networks are required to support WPA2, so the choice of WPA can only be determined by non-standard situations. Eg, OS older than Windows XP SP3 do not support WPA2 without applying patches, so machines and devices managed by such systems require the attention of a network administrator. Even some modern smartphones may not support the new encryption protocol, this mainly applies to off-brand Asian gadgets. On the other hand, some Windows versions older than XP do not support WPA2 at the object level group policy, so in this case they require more fine tuning network connections.
The technical difference between WPA and WPA2 is the encryption technology, in particular, the protocols used. WPA uses the TKIP protocol, WPA2 uses the AES protocol. In practice, this means that the more modern WPA2 provides more high degree network protection. For example, the TKIP protocol allows you to create an authentication key up to 128 bits in size, AES - up to 256 bits.
Conclusions website
- WPA2 is an improvement over WPA.
- WPA2 uses the AES protocol, WPA uses the TKIP protocol.
- WPA2 is supported by all modern wireless devices.
- WPA2 may not be supported by older operating systems.
- WPA2 is more secure than WPA.
Good day, dear readers of the blog site! Today we will talk about DIR-615 wireless security, about network security
generally. I will tell you what the concept of WPA is. Next I will give step by step instructions setting up a wireless network using a wizard, about automatic and manual modes assigning a network key. Next we will show how add a wireless device using the WPS wizard. Finally, I will provide a description of the WPA-Personal (PSK) and WPA-Enterprise (RADIUS) configurations.
Network Security
In this article, as promised, I will write about the different levels of security that you can use to protect your data from intruders. DIR-615 offers following types security:
What is WPA?
WPA, or Wi-Fi Protected Access Wi-Fi access), - This Wi-Fi standard, which was designed to improve security capabilities WEP.
2 major improvements over WEP:
- Improved data encryption via TKIP. TKIP mixes the keys using a hashing algorithm and adding an integrity check feature, thereby ensuring that the keys cannot be tampered with. WPA2 is based on 802.11i and uses AES instead of TKIP.
- User Authentication, which is generally absent in WEP, through EAP. WEP regulates access to a wireless network based on the computer's specific hardware MAC address, which is relatively easy to find out and steal. EAP is built on more secure system public key encryption to ensure that only authorized network users can access the network.
WPA-PSK/WPA2-PSK uses a passphrase or key to authenticate your wireless connection. This key is an alphanumeric password between 8 and 63 characters in length. The password can include characters (!?*&_) and spaces. This key must be exactly the same key that is entered on your wireless router or access point.
WPA/WPA2 enables user authentication via EAP. EAP is built on a more secure public key encryption system to ensure that only authorized network users can access the network.
Wireless Setup Wizard
To launch the security wizard, open the morning Setup and then click the button Wireless Network Setup Wizard .
Automatic Network Key Assignment
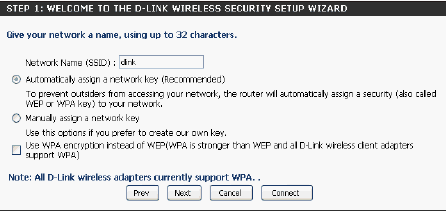
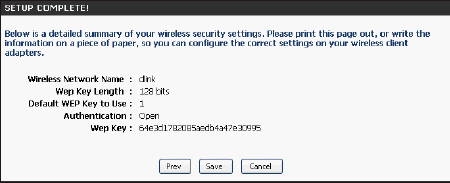
Once this screen appears, the installation is complete. You will be provided with a detailed report of your network security settings.
Click Save
, to continue.
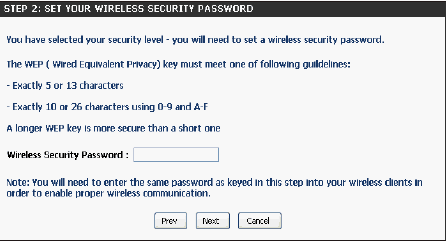
Manual Network Key Assignment

Select a wireless security password. it must be exactly 5 or 13 characters long. It can also be exactly 10 or 26 characters using 0-9 and A-F.
Click to continue.
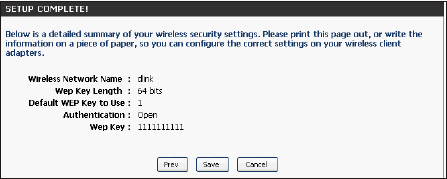
Installation completed. You will be provided with a detailed report of your wireless security settings. Click Save to complete the Security Wizard.
Add a Wireless Device using the WPS Wizard
Select Auto to add a wireless client using WPS. Once you have chosen Auto and pressed Connect You will need a maximum of 120 seconds of time to apply the settings to your wireless client(s) and successfully establish a connection.
If you choose Manual , a screen with a summary of the settings will appear. Write down the secret key and enter it on your wireless clients.
