1. Statement of the problem
Introduction
Backup technologies4
1 Overview of backup technologies
2 Technologies for storing backups and data
2.2 Disk drives
2.3 Network technologies
3 Backup storage
4 Restoring data from backups
4.1 Data recovery on a clean computer
Types of backup programs
1 GFI Backup Review
1.1 General characteristics
1.2 Practical use
2 Review of Paragon Drive backup Workstation
2.1 General characteristics
3 Acronis True Image review
3.1 General characteristics
Application and comparison of the reviewed software products
Conclusion
Bibliography
1. Statement of the problem
Task 3.5 "Tasks and means of data backup and storage." Learn the basic tasks and methods of data backup and storage. Review and Compare software well-known manufacturers (Microsoft, Veritas, Symantec, etc.). Write a description of the practical application of the available tool.
2. Introduction
media backup storage
Backup is the process of creating a coherent (consistent) copy of data. Backup is becoming increasingly important as data volumes increase significantly in the computer industry. The backup subsystem is a very important part of any information system. When properly organized, it can solve two problems at once. Firstly, reliably protect the entire range of important data from loss. Secondly, to organize a quick migration from one PC to another if necessary, that is, to actually ensure uninterrupted work for office employees. Only in this case can we talk about efficient work Reserve copy. Mastering backup tactics is an essential attribute of professionalism for the user and system administrator. It follows from the user’s decision for himself, by what methods and at what level the information will be stored (the required software and hardware depends on this), the volume of information necessary for saving (the selected information media depends on this), size and structure local network(the actual mechanism for systematically performing copying depends on this).
To perform the backup procedure, special hardware and software subsystems called backup subsystems are usually created. They are designed specifically for both regular automatic copying of system and user data, and for rapid data recovery. Storing information separately from system files is already a mandatory rule. When regular user this means, at a minimum, dividing the HDD into three logical drives: for the system, for applications, for data. In the case of a corporate employee with a large amount of confidential information, placing the information on other, non-system physical disks. This measure also facilitates the data archiving operation itself. The principle of separate storage of information applies to both file archives and disk images. They must also be stored at least on non-system partitions of one HDD. In the case of a corporate user, the principle of separate storage of information should be implemented even more strictly: at least one of the copies should be stored in a separate place so as not to lose corporate information in case of unforeseen circumstances.
3.Backup technologies
1 Overview of backup technologies
Depending on the importance of the information stored on the computer and the frequency of its use, several types of data backup are performed:
Full backup.
Differential backup.
Incremental backup.
1.1 Full backup
It is the main and fundamental method of creating backup copies, in which the selected data array is copied entirely. This is the most complete and reliable type of backup, although it is the most expensive. If it is necessary to save several copies of data, the total stored volume will increase in proportion to their number. To prevent a large amount of resources used, compression algorithms are used, as well as a combination of this method with other types of backup: incremental or differential. And, of course, a full backup is indispensable when you need to prepare a backup copy for quickly restoring the system from scratch.
Advantages of the method:
Easily search for files - Because everything on your device is backed up, you don't have to browse through multiple media to find the file you need.
A current backup of the entire system is always located on a single media or set of media - If you need to restore the entire system, all the necessary information can be found in the latest complete backup copy.
Disadvantages of the method:
Redundant data protection - since most system files change rarely, each subsequent full backup is a copy of the data saved during the first full backup. A full backup requires a large amount of storage space.
Full backups take longer - Full backups can take a long time to complete, especially if you select devices on the network for storage.
1.2 Differential backup
It differs from incremental in that data is copied from the last moment of Full backup. The data is stored in the archive on a “cumulative basis”. On Windows family systems, this effect is achieved by the fact that the archive bit is not reset during differential copying, so the changed data ends up in the archive copy until a full copy resets the archive bits. Due to the fact that each new copy created in this way contains data from previous, this is more convenient for completely restoring data at the time of the accident. To do this, you only need two copies: the full one and the last of the differential ones, so you can bring data back to life much faster than gradually rolling out all the increments. In addition, this type of copying is free from the above-mentioned features of incremental copying, when, with a complete recovery, old files are reborn from the ashes. There is less confusion. But differential copying is significantly inferior to incremental copying in saving the required space. Since each new copy stores data from previous ones, the total volume of reserved data can be comparable to a full copy. And, of course, when planning the schedule (and calculating whether the backup process will fit into the time “window”) you need to take into account the time to create the last, largest, differential copy.
Advantages of the method:
Easily search files - To restore a system protected with a differential backup strategy, two backups are required - the latest full backup and the latest differential backup. Recovery time is significantly faster than backup strategies that require the last full backup and all incremental backups created since the last full backup.
Faster backup and recovery times - Differential backups take less time than full backups. Disaster recovery is faster because only the latest full backup and differential backup are needed to completely restore the device.
Disadvantage of the method:
Redundant data protection - All files changed since the last incremental backup are preserved. This creates redundant backups.
1.3 Incremental backup
Unlike a full backup, in this case not all data (files, sectors, etc.) are copied, but only those that have changed since the last copy. To determine the copying time, you can use various methods, for example, in systems running operating systems The Windows family uses a corresponding file attribute (the archive bit), which is set when the file has been modified and cleared by the backup program. Other systems may use the date the file was modified. It is clear that a scheme using this type of backup will be incomplete if a full backup is not carried out from time to time. When performing a full system restore, you need to restore from the last copy created by Full backup, and then one by one restore data from incremental copies in the order in which they were created. This type is used to reduce the amount of space consumed on information storage devices when creating archival copies (for example, reduce the number of tape media used). This will also minimize the time it takes to complete backup jobs, which can be extremely important when the machine is constantly running or when pumping large amounts of information. Incremental copying has one caveat: step-by-step recovery also returns the necessary deleted files during the recovery period. For example: let’s say a full backup is performed on weekends, and an incremental one on weekdays. The user created a file on Monday, changed it on Tuesday, renamed it on Wednesday, and deleted it on Thursday. So, with a sequential, step-by-step data recovery for a weekly period, we will receive two files: with the old name on Tuesday before the renaming, and with a new name created on Wednesday. This happened because different incremental copies stored different versions the same file, and eventually all variants will be restored. Therefore, when sequentially restoring data from an “as is” archive, it makes sense to back up more disk space, so that deleted files can also fit.
Advantages of the method:
Efficient use of media - Because only files that have changed since the last full or incremental backup are saved, backups take up less space.
Faster backup and recovery time - Incremental backups take less time than full and differential backups.
Disadvantage of the method:
Backup data is stored on multiple media - Because backups are located on multiple media, it may take longer to restore your device after a disaster. Additionally, to effectively restore the system, the media must be processed in the correct order.
3.2 Technologies for storing backups and data
In the process of backing up data, the problem of choosing a technology for storing backup copies and data arises. Currently, the following types of media are especially popular:
Magnetic tape drives.
Disk drives.
Network technologies.
2.1 Tape drives
Not only in large corporations, but also small businesses are well aware of the need for backup and recovery of information. In enterprise-scale systems and networks of large departments, in small companies and individual users, streaming drives, or streamers, are equally successful. Their design is based on a tape drive mechanism operating in inertial mode. Magnetic tape drives have been used together with computers since the early 50s - it was then that they began to replace “paper” storage media - punched tapes and punched cards. An important factor that ensures such long-term interest in magnetic tape drives is the low cost of storing information. The main problem with using tape drives today is that many of them use incompatible tape formats. This often makes it difficult not only to select a specific drive, but also to exchange data during its operation. A lot of efforts have been made to solve this problem, but in general it can be stated that fundamental changes have not yet occurred (although there is some progress in this direction). The most widely used technologies today are Travan, DLT (Digital Linear Type), DAT-DDS ( Digital Audio Tape-Digital Data Storage), LTO (Linear Tape Open), Mammoth and AIT (Advanced Intelligent Tape). To make an informed choice of a backup system, you need to clearly understand the advantages and disadvantages different devices, which are largely determined by the capacity of the system, its speed, reliability and price. The main drivers for improving the performance of mid-range and high-end tape devices are the widespread use of the Internet and the proliferation of corporate intranets, the increase in the number of servers (needed to support the growth of these networks), and the tightening requirements for information storage and its recovery in the event of disasters. The demand for backup and storage systems is particularly driven by the increasing use of applications such as multimedia, video on demand, audio content, image processing, etc. Two methods of recording on magnetic tape are used: slant and linear serpentine. In oblique recording systems, multiple read/write heads are placed on a rotating drum mounted at an angle to a vertical axis (a similar arrangement is used in consumer video equipment). The movement of the tape when writing/reading is possible only in one direction. In linear serpentine recording systems, the read/write head is stationary when the tape moves. Data on tape is recorded in the form of many parallel tracks (serpentine). The head is placed on a special stand; when the end of the tape is reached, it moves to another track. The tape moves when writing/reading in both directions. In fact, several such heads are usually installed so that they serve several tracks at once (they form several write/read channels).
low cost.
low power consumption of the drive.
large amounts of data.
An easy way to increase the amount of data you store without making a significant investment.
Disadvantages of storing data on tape:
low data access speed.
complex process of processing parallel data queries.
3.2.2 Disk drives
There are two most common types of disk drives: hard drives magnetic disks and optical drives.
Hard disk drives (Hard Disk Drive, HDD) are the main devices for operational storage of information. Modern single drives are characterized by volumes from hundreds of megabytes to several gigabytes with access times of 5-15 ms and data transfer rates of 1-10 MB/s. Regarding the server case, a distinction is made between internal and external drives. Internal drives are significantly cheaper, but they are maximum amount limited by the number of free compartments in the case, the power and the number of corresponding connectors of the server power supply. Installing and replacing conventional internal drives requires shutting down the server, which is unacceptable in some cases. Internal drives with the possibility of “hot swap” (Hot Swap) are ordinary hard drives installed in special cassettes with connectors. Cassettes are usually inserted into special compartments on the side of the front panel of the case; the design allows the drives to be removed and inserted while the server is powered on. For standard cases, there are inexpensive devices (Mobile Rack) that provide quick removal of standard hard drives. External drives have their own cases and power supplies; their maximum number is determined by the capabilities of the interface. Service external drives can also be done while the server is running, although it may require stopping access to some of the server’s disks.
For large volumes of stored data, external storage units are used - disk arrays and racks, which are complex devices with their own intelligent controllers that, in addition to normal operating modes, provide diagnostics and testing of their drives. More complex and reliable storage devices are RAID arrays (Redundant Array of Inexpensive Disks - a redundant array of inexpensive disks). For the user, RAID is a single (usually SCSI) disk in which simultaneous distributed redundant writing (reading) of data is performed on several physical drives (typically 4-5) according to rules determined by the implementation level (0-10). For example, RAID Level 5 allows you to correct errors during reading and replace any disk without stopping data access.
CD-ROM drives extend the capabilities of NetWare storage systems. Existing drives provide read speeds from 150 kB/s to 300/600/900/1500 Kbyte/s for 2-, 4-, 6- and 10-speed models with an access time of 200-500 ms. NetWare allows you to mount a CD as a network volume that can be read by users. The volume capacity can reach 682 MB (780 MB for Mode 2). CD-ROM devices are available with various interfaces, both specific (Sony, Panasonic, Mitsumi) and general ones: IDE and SCSI. The NetWare server only supports CD-ROMs with SCSI interfaces; new drivers also exist for the IDE; devices with specific interfaces can only be used in DOS for system installation. From a performance point of view, it is preferable to use CD-ROM SCSI, but they are significantly more expensive than similar IDE devices. On a server with SCSI disks, using a CD-ROM with an IDE interface may not be possible due to adapter conflicts.
The advantages of such drives are:
quick access to data.
possibility of parallel access to data without significant loss of speed.
Disadvantages of disk drives:
higher cost than tapes.
higher power consumption.
more expensive storage expansion.
impossibility of ensuring high security of copies.
3.2.3 Network technologies
Network-attached storage is built on three fundamental components: switching, storage, and files. All storage products can be represented as a combination of the functions of these components. This can be confusing at first: because storage products were developed in completely different directions, features often overlap.
The network runs many client-server applications and various types of distributed applications, but storage is a unique and specialized type of application that can function across multiple network environments. Since storage processes are tightly integrated with networks, it is appropriate to recall that network storage is system applications. The services provided by network storage applications can be used by complex enterprise programs and consumer applications. As with many technologies, certain types of systems are better suited to the demands of complex, high-level applications.
The term "switching" applies to all software and hardware and to services that provide storage transport and management on network-attached storage. This includes various elements such as cabling, network I/O controllers, switches, hubs, address fetching hardware, data link control, transport protocols, security, and resource reserves. SCSI and ATA data bus technologies are still widely used in networked storage and are likely to continue to be used for a long time. In fact, SCSI and ATA products are used much more frequently in NAS technology today. There are two important differences between SAN storage networks and regular LANs. Storage area networks (SANs) automatically synchronize data between separate systems and storage locations. Network storage requires components high degree precision to provide a reliable and predictable environment. Despite its distance limitations, parallel SCSI is an extremely reliable and predictable technology. If new switching technologies such as Fiber Channel, Ethernet, and InfiniBand replace SCSI, they will need to demonstrate similar or best level reliability and predictability. There is also a point of view that considers switching as a storage channel. The very term “channel”, which originates in the environment of large computers, implies high reliability and performance.
Storage primarily affects address space block operations, including virtual environment creation where logical storage block addresses are mapped from one address space to another. Generally speaking, the storage functionality of network attached storage hasn't changed much, except for two notable differences. The first is the ability to find device virtualization technologies, such as device management inside network storage equipment. This type of feature is sometimes called storage domain controller or LUN virtualization. The second major differentiator for storage is scalability. Storage products, such as storage subsystems, have significantly more controllers/interfaces than previous generations of bus technology, as well as much larger storage capacity.
The file organization function presents an abstract object to the end user and applications, and organizes the layout of data on real or virtual storage devices. The bulk of the functionality of files in network storage is provided by file systems and databases; they are complemented by storage management applications such as backup operations, which are also file applications. Network storage has made little difference to file functions to date, with the exception of the development of NAS file systems, particularly Network Appliance's WAFL file system. In addition to the mentioned NAS and SAN storage technologies, aimed at large and wide area networks, in small local networks the dominant position is occupied by DAS technology, according to which the storage is located inside a server that provides the storage volume and the necessary computing power.
The simplest example of a DAS would be a hard disk drive inside a personal computer or tape drive connected to a single server. I/O requests (also called commands or data transfer protocols) directly access these devices. However, such systems do not scale well, and companies are forced to purchase additional servers to expand storage capacity. This architecture is very expensive and can only be used to create small data warehouses.
3 Backup storage
When backups are made, these copies must be retained. However, it is not at all so obvious what exactly should be stored and where. To correctly determine where to store copies, you must first consider the circumstances under which the backups will be used. Three main situations can be distinguished:
Recovery separate files at the request of users.
Global emergency recovery.
Archive storage will likely never be needed.
Unfortunately, there are incompatible contradictions between the first and second situations. When a user deletes a file by accident, he wants to get it back immediately. Therefore, the backup media should be no more than a few meters away from the computer on which the data is to be restored. In the event of an emergency, you will need to perform a full recovery of one or more computers in your data center, and if the failure occurs is physical, it will destroy not only the computers, but also all backups stored nearby. The issue of archive storage is less controversial - the likelihood of an administrator using it is quite low, so if the backup media is stored far away from the data center, this should not be an issue. Different approaches may be chosen to address these different challenges, depending on the needs of the organization. The first possible approach is to store several days' worth of copies on site, and then move those copies to more secure off-site storage when new daily copies are created. Another approach is to support two media sets:
A collection of media in a data center used solely for on-demand recovery of individual data
A set of media for remote storage and recovery in case of emergencies
Of course, having two sets means having to back everything up twice or copy it. It can be done, but double backups can take a long time, and copying backups may require multiple devices to handle the backups (and perhaps dedicate a separate computer to copying. The challenge for a system administrator is striking a balance between meeting the needs of users and availability of backup copies in case of worst-case scenarios.
3.4 Restoring data from backups
In most cases, backups are performed daily, and restores tend to occur less frequently. However, recovery is inevitable, there will definitely be a need for it, so it is better to prepare for it. Here it is important to analyze two important situations that arise when restoring data from backups:
Recovering data on a clean computer.
Checking the relevance of backups.
3.4.1 Restoring data on a clean computer
Blank computer data recovery is the process of restoring a complete copy of the system on a computer that has absolutely no data - no operating system, no applications, nothing. In general, there are two main approaches to recovery on a bare computer:
Reinstallation followed by recovery, here the base operating system is installed in the same way as on a completely new computer. Once the operating system is installed and properly configured, the remaining drives can be connected and formatted, and all copies can be restored from backup media.
A system recovery disk is some kind of bootable media (usually a CD-ROM) that contains a minimal system environment and allows you to perform most basic administrative tasks. The recovery environment contains the necessary utilities for partitioning and formatting disks, the device drivers needed to access the backup device, and the programs needed to restore data from backup media.
4.2 Checking the relevance of backups
All types of copies should be reviewed periodically to ensure that the copies can be read and are current. Indeed, sometimes copies, for one reason or another, may not be readable; most often this is discovered only when data is lost, when a backup copy is required. The reasons for this can be very different, for example: the tape drive head is misaligned, an incorrectly configured backup program and operator error. But whatever the reason, without periodic checks, the administrator cannot be sure that there really are backups from which data can be restored someday later.
4. Types of backup programs
Today, there are many software products to provide data backup technology. At the corporate level, products such as:
Acronis True Image Home.
Paragon Drive Backup Server Edition.
Symantec Backup Exec.
Windows System Recovery.
For network backup:
Paragon Drive Backup Enterprise Server Edition.
Acronis Backup & Recovery.
A further review of backup technologies will be based on a description of the practical use of the following three software products:
Paragon Drive backup Workstation.
Acronis True Image Home.
4.1 GFI backup program overview
4.1.1 General characteristics
System requirements:
Microsoft Windows 7 (x86 or x64), Server 2008
(x86 or x64), Vista (x86 or x64), Server 2003 Standard/Enterprise
(x86 or x64), XP (x86 or x64)
Processor - Intel Pentium 4 or similar
Memory - 512 MB
Physical memory - 100 MB for installations
Secure and reliable data backup and recovery. Backup provides centralized management of backup and recovery as information loss protection, preventing the loss of data such as spreadsheets, projects and images. This process involves creating a backup from the source to a selected location.
Data synchronization.
File synchronization is the process of maintaining a current set of files across multiple locations, such as a workstation and laptop. If a user adds, deletes or modifies a file in one location, GFI Backup adds, deletes or modifies the same file in all other locations. Using the GFI Backup Agent, users can create their own synchronization tasks in addition to centralized backup operations.
Backup to any data storage device; backup via FTP.Backup allows you to backup to internal and external hard disks, to disks on the local network, network devices data storage, media/DVD/Bluray, portable devices (USB devices, memory cards, flash memory, floppy disks, etc.), as well as to remote locations using FTP with an automatic renewal system.
Using standard Zip archives.
Unlike other backup programs, GFI Backup does not use its own archive formats, but uses the standard Zip format. This allows
restore data manually even if GFI Backup is not installed. You can choose to create self-extracting archives, as well as backup without data compression for speed and redundancy. When using Zip archives, GFI Backup is able to split and save files onto multiple media. 4.1.2 Practical use of the program
In order to evaluate the capabilities of the program, we will need:
A personal computer with an installed operating system and a set of necessary user software.
Bootable Windows disk P.E.
The installer of the program itself, which can be downloaded from the official website of the program, or from other Internet resources.
We use a Windows PE boot disk to launch the working environment, since the developer did not include support for a boot disk with this product. GFI Backup can also work under the OS installed on the computer, but the functionality will be reduced to managing client machines.
As an example of such a program for backing up data, we will use GFI Backup Home Edition. The program is free and intended exclusively for non-commercial use, as indicated by the Home Edition prefix. It follows from this that the functions declared by the developer are not presented in full. You can download it from the manufacturer’s website #"justify">The main program window is not overloaded unnecessary functions. All the main features of the program are available immediately upon download, and in the form of “wizards”.
Fig. 1 (Main window of the program).
To create an image, select - Backup , which is used to create a backup copy of data. When you click it, a wizard is launched that allows you to select copy objects and save location. The combination of source and destination locations is called task (task). On the General tab, the name of the task is indicated, as well as the name of the archive copy. Fig.2 (Backup Settings Wizard). In the Source tab, you need to select the location of the data that will be archived, for example, a copy of the entire C:\ drive. The program can also archive registry keys, data mail clients and user settings. Archiving emails - especially useful feature. Supported email clients: Outlook, Windows Mail and Thunderbird. Fig 3. (Selecting email clients). Save option available custom settings various programs - from browser bookmarks to Total Commander settings. Fig. 4. (Window for selecting user program settings). After selecting the data to be archived, in the lower left corner of the window you can immediately see the number and volume of elements that will be copied. On the Destination tab, you select a location to store the archive that will be obtained as a result of archiving. It can be placed on: Local disk (logically, this should not be the same disk from which the data copy is made). Remote Windows network folder. Removable media such as a flash drive or memory card/DVD/Blu-Ray disc(s). FTP server. Select saving to local disk. The Options tab contains important options. The first one is whether to compress the data or not. A compressed archive will take up less space, but it will also take more time to create. It is also possible to protect the archived copy with a password - either a Zip password (frivolous protection, in fact), or encryption using the AES algorithm (guessing a password for a person who is not supposed to see the contents of the archive will become a much more difficult task). The program is made in such a way that full copying is carried out only with compression and encryption, differential copying with encryption, but without compression; and incremental copying without encryption and without compression. This was done to save system and user resources. Figure 5. (Copy options). Scheduler tab. Here you can select the frequency of copying. Among the options there is run once , run manually , at Windows startup/shutdown, by day of the week, once every N days and once every N hours. The frequency should be chosen based on the importance of the data and its volume (for example, copying 20 gigabytes of data every hour will only accelerate disk failure from overload). Events tab. Here you can specify ways to indicate what is happening. For example, the program can send an e-mail to a specified address when errors occur or the archiving process is completed. After viewing all the tabs and setting the desired options, the created task can be viewed by clicking on the button My Tasks in the main program window. If the task was configured to be launched manually, you can launch it in the same window by clicking the button Start . The archiving process will be displayed at the bottom of the window, as well as in the line with a description of the task. Fig 6. (Task window). To evaluate the performance of the program, 3 backup copies were made: Full (MyBackup1 with compression) . Differentiated (MyBackup2, with and without compression). Incremental (MyBackup3 with and without compression). Fig 7. (Browse files local disk P). Time and speed of creating backups: Full copying with compression - 34 min.; copy speed - 4.01 Mb/s. Differentiated copy without compression - 14 min.; copying speed - 12 Mb/s. Differentiated copy with compression - 18 min.; copy speed - 8 Mb/s. Incremental copy without compression - 8 min.; copy speed - 4.9 Mb/s. Incremental copy with compression - 12 min.; copying speed - 6 Mb/s. The recovery process is very simple, just select in the main program window Restore and indicate which archive needs to be restored. When restoring files, the partition is formatted automatically and the size of the resulting volume will be the same as during copying. As a result of experiments, this product did not perform well. After four attempts to restore each of the archives, we get the following picture: The archive of a full copy was restored without errors in 4 cases. A differentiated copy without compression out of four cases was fully functional in only two cases, but in other cases some files were damaged. The differentiated copy with compression was successfully restored in only one out of four cases. Both incremental copies were unable to restore the OS bootloader. Based on this and taking into account the limited functionality of the free version of the program, we can conclude that this program Suitable only for backing up files and folders with user data, but not for copying the entire volume. 4.2 Review of Paragon Drive backup Workstation 2.1 General characteristics The purpose of the Paragon Drive Backup program is to backup and restore operating systems and user data through the image mechanism. Along with this, Paragon Drive Backup has a number of other functions: copying and restoring individual files, basic capabilities for managing and editing partitions, functions for restoring the operating system bootloader, the ability to migrate from one computer to another (p2p) and to a virtual environment (p2v). The Paragon Drive Backup family includes two products: Drive Backup Workstation and Drive Backup Server. The Drive Backup Server option differs in that it supports work with server operating systems, and also includes migration functions to a virtual environment (p2v). Otherwise, the functions of the programs are the same. Drive Backup works on all operating systems Windows systems starting with XP and ending with Windows 8 and Server 2008 R2. The following file systems are supported:(v1.2, v3.0, v3.1) FAT16Ext2FSExt3FSExt4FSSwapHFS+ Paragon Drive Backup can also work without installation in OS. It is enough to unpack the program image onto a flash card or other media and boot from it. There are two types of Paragon Drive Backup images: Standard Linux-based (created through the Disk Creation Wizard). Extended on Windows based PE (downloaded from the manufacturer’s website). Support hard drives MBR and GPT (including those with a capacity of 2.2 TB or more). Hard drives with IDE, SCSI and SATA interfaces. Solid State Drives (SSD). AFD (Advanced Format Drive) drives. Disks with a sector size other than 512 bytes. CD-R, CD-RW, DVD-R, DVD+R, DVD-RW, DVD+RW, double-layer DVD-R, DVD+R, and Blu-ray discs. Hard drives FireWire (IEEE1394), USB 1.0, USB 2.0, USB 3.0. PC card storage devices (MBR and GPT flash memory, etc.) . System requirements: OS: Windows 2000 (32 bit version) Windows XP (32 and 64 bit version) Windows Vista (32 and 64 bit version) Windows 7/8 (32 and 64 bit version) Intel Pentium processor or equivalent with a frequency of at least 300 MHz Hard drive with 250 MB of available disk space 2.2 Practical use Installed in the operating system, Paragon Drive Backup allows you to create an image without stopping the operating system. This is achieved using Paragon Hot Backup technology, as well as Windows shadow backup technology - Microsoft Volume Shadow Copy Service. The latest technology is available starting with Windows Vista. Figure 8. (Program start window) The program allows you to create both full and differentiated or incremental backups. If you create a differential copy, only changes since the last backup are recorded in the archive. In the case of incremental - changes since the last full archiving. The archive can be sector-by-sector (the entire disk structure is copied, regardless of the file system), or file-based. Differential copying is applicable only to sector-by-sector archives, and incremental copying, which is called “file addition” in the program, is applicable only to file archives. There are also complex archives that combine sector-by-sector and file backup. Let's create a full backup of drive C, including the MBR. As a result, a complex archive will be created, within which the MBR will be recorded as a sector-by-sector archive, and everything else as a file archive. Figure 9. (Image files). Figure 9 shows that the folder contains files of two extensions: *.PBF and *.PFM. The main ones are files with the extension *.PBF (paragon backup file). Inside these files are the contents of files and sections. Files with the *.PFM extension are additional archive description files that are used by the Image Explorer utility to quickly display information about the archive. When restoring data, files with the *.PFM extension are not required. Archive.pbf is the main file that links img_0... and img_1... ._0 - contains an archive of files, and img_1 is a copy of the MBR. When restoring, we specify each of these files in the dialog box, which is not always convenient. You can also perform backups on a schedule - this is called a cyclic backup. The result of such copying is two images: The first image is complete, and the second is differentiated. This type of archiving is available only for entire disks. Fig. 10.(Setting up scheduled copying). As a result of creating a disk image and restoring from it, it is clearly visible that the program does not perform both operations immediately. First, the program, by analyzing the file attributes, creates a list of changes and only then, after the parameters necessary for the operation have been set, clicking the “Apply” button starts copying. However this mode can be disabled in the settings and the image creation process will take less time. Figure 11. (Window to start backup). Archive creation can be performed not only from under installed Windows. You can also create a boot disk, bootable Flash media, or create a so-called archive capsule. A backup capsule is a special boot partition on your hard drive that contains a standalone running version of Paragon Drive Backup and storage space for backup copies. A capsule can be created as a primary partition or a logical partition within an extended partition hard drive and be located anywhere on the hard drive: at the end, at the beginning or between other partitions. Next, we try to create a backup capsule. Fig 12.(Archive capsule settings window) If there is no free space on a hard disk partition, then an archive capsule is created by free space other partitions of the hard drive. We create a capsule with the image on the free space of the hard drive D:\. After creating the capsule, you need to restart the computer and press the F1 key, while selecting the OS to boot, to boot into the capsule. The process of restoring an image from a capsule is the same as in the Windows program. This method is widely used by manufacturers of laptops and personal computers. Now let's try to create boot image programs (rescue disk). Bootable media can be created on a CD or on a Flash drive. When creating a disk, you can immediately add the necessary files to it. Figure 13. (Rescue disk creation wizard). Now you need to restart your computer and select the option to boot from external media. When booting from a disk, all necessary operations for backing up and restoring images are available, and the function of managing and editing hard disk partitions becomes possible. Figure 15. (Main program window.) All operations are accessible and easy to perform. However, the process of creating an image takes much less time than creating it from an installed OS. Archiving in the boot disk is carried out on local media; the image can also be saved to a network folder. However, working with network resources implemented extremely inconveniently. You must manually set paths to network resources in order to mount them to a local folder. There is a “Browse Network” button, but it doesn’t work. Figure 16. (Connecting network storages) The function of direct editing of sectors on the hard drive is also available. Fig 17.(Sector editor hard section disk) Bootable disk Paragon Drive Backup allows you to restore Windows boot without restoring from a backup image, that is, there are functions automatic search installed copies of Windows, manual editing of boot.ini, etc. However, out of three attempts to restore the damaged boot.ini file, not one was successful. Figure 18. (Windows Boot Recovery Wizard) The developer included in the image the function of deploying the system on new equipment (p2p). In other words, the system image with all installed software can be unpacked onto other personal computers, which is important in the work of system administrators. Preparation for booting the system on new hardware is done on a deployed image. Those. First you need to deploy the image on a new PC, and then carry out the p2p procedure. By and large, the p2p procedure comes down to installing necessary drivers for new equipment. First we need to select which copy of the OS on the hard drive we will restore, and then specify the drivers. Drivers can be downloaded automatically (from a specified folder) specifically for the hardware used on the new PC. Fig 19.(Menu for selecting actions when loading drivers) Based on the experiments performed, we can conclude that this product performs the stated functions quite well, except for the network copy function and the system boot recovery function without affecting the image. For each backup type, four copy and restore attempts were made. All attempts were successful. Product advantages: P2P technology is included in the price and comes with the product. Ready-to-use boot disk based on Windows PE. Flexible pricing and licensing policy. Product Disadvantages: Storing the archive in several files. OS restoration tools do not work without the need to restore from an image. Working with network resources is implemented extremely poorly. Complex software interface. 3 Acronis True Image Home review Acronis program True Image Home is designed to create a backup image of the system, local disk, and files. It can automatically, at a given time, archive the necessary data (system, disk, folder, file). Archiving can be done in different ways: create a new image every time; update an existing one by creating a small image that includes only the changes that have occurred to the data since the creation of the previous image. In addition to creating images, Acronis can restore data that was archived in an image. When creating a backup image of the system, all files from the specified disk are saved to the archive, that is, all programs, all registry paths, all system settings made before archiving the disk. One of the common ways to use the program in practice is to restore the system from a previously created image, booting from DOS from a special Acronis boot disk. In this case, in approximately 25 - 40 minutes, the system is restored with all the settings, drivers and software that were in the system at the time the archive was created. Supported Operating Systems: Windows® Vista/7 32 & 64 bit Windows® XP SP 2, SP 3 Windows® XP Professional x64 Edition SP2 Acronis True Image Home allows you to create bootable CDs for complete recovery of information on hard drives/partitions created by Windows XP/Vista/7. Minimum system requirements: Pentium processor or higher; RAM 256 MB; Optical drive with the ability to write CD-R/RW or DVD +R/RW for creating bootable discs. Supported Hardware: Internal and external hard drives; Network drives and storage devices; CD-R(W), DVD+R, DVD+RW, DVD-RAM, BD-R (Blu-ray); ZIP® Jazz® and other removable storage media; P-ATA (IDE), S-ATA, SCSI drives, removable media with IEEE1394 (Firewire) and USB 1.0 / 2.0 interface, flash memory cards; Supported file systems: FAT16/32, NTFS, Linux Ext2, Ext3, ReiserFS, Linux SWAP; Sector-by-sector copying for unknown or damaged file systems 3.2 Practical use After installing the program and restarting the system, Acronis TrueImage is ready to use. Figure 20. (Main program window) The right window contains icons, double-clicking on which launches basic operations. When you single-click an icon on the right side of the main program window, a hint appears on the left side, informing you about the purpose of the selected icon. From the main program window you can perform the following actions: Create image - launches the image creation wizard, which makes an exact copy of the entire hard drive or a separate partition and saves it to a file on the hard drive, in the security zone, on network drive or on removable media. Restore image - launches the image recovery wizard. The wizard requests options for restoring a partition or the entire hard drive from an image file that was created earlier and starts the recovery process. Mount image - launches the Mount Image Wizard, which assigns the file image of a tough disk or partition, letter and uses the image as a regular disk. Disconnect image - launches the wizard for disabling an image that was previously connected. Clone disk - launches the disk cloning wizard. This wizard helps you transfer all data from one hard drive to another and create an exact copy of it. Install new disk- launches the installation wizard for new disks, with which you can prepare a new one for further work HDD installed on the computer. The wizard will create partitions on your hard drive and format them. Assign task - starts the Scheduler. With it you can schedule for a specific time automatic start image creation or create a task, which can then be launched manually without setting up the image creation wizard each time. Acronis Secure Zone - launches the Acronis Secure Zone Management Wizard. Acronis Secure Zone is an area on your hard drive reserved by Acronis TrueImage where the program saves images of partitions or the entire hard drive. This area is not accessible to other programs and therefore the image file located in the security zone will not be accidentally deleted or corrupted. Using this wizard, you can manage the size of the security zone, increasing or decreasing the space it occupies on the selected partition, or moving the security zone to another disk or partition. Startup Repair - launches the Activate Startup Repair wizard. After specifying the parameters requested by this wizard, the data recovery from the image will be scheduled before the operating system boots. Image Verification - launches the Image Verification Wizard, which verifies the integrity of partition or hard disk image files. Create a bootable disk - launches the corresponding wizard, which creates bootable floppy disks or a bootable CD. Floppy disks or a disk can come in handy during a serious crash when the system cannot boot from the hard drive. With their help, you can start the process of restoring the system from a previously created image. View Log - This shortcut allows you to open the log and view all the events that occurred during Acronis work TrueImage. In order to create an image of a partition or the entire hard drive, you need to double-click on the Create image icon in the main program window. Figure 21. (Image Creation Wizard) To create an image of one or more partitions or the entire hard drive, you need to mark them in this window. Once the objects are selected and the Next button is clicked, the following wizard window will open. If images have not been created previously, the following information message will be displayed: Figure 22.(Information message) Figure 23. (Selecting a location to store the image) In this wizard window, you need to specify the location of the image file and its name. If you select Acronis Secure Zone, the image will be created in a specially designated location on your hard drive. No other programs have access to this area of the disk and therefore the image file will not be modified or deleted. After clicking the Next button, the following wizard window will open. Figure 24. (Selecting backup mode) In this window you can select the image type. If an image of the selected partition or hard drive has not been created before, then you need to select Create a full backup. If the image has already been created and needs to be updated, then you need to check the Add changes to an existing archive in an incremental way. After clicking the Next button, the following wizard window opens. Image files are very large, sometimes exceeding a hundred gigabytes. At this stage of image creation, you can split the file into parts by specifying the size of one part. If you select Automatic, Acronis TrueImage will decide whether to split the image file into parts during image creation. For example, if the image is saved on a partition with a file NTFS system, then regardless of the size of the image file, it will be saved as one file. If the image is saved on a partition with the FAT32 file system, the image file will be automatically cut into parts, each of which will be 4 Gigabytes in size. This is due to the restrictions that the FAT32 file system imposes on the maximum size of a single file. After clicking Next, the wizard will display the following window. Figure 26. (Selecting the compression ratio of the image) Similar to archivers, Acronis TrueImage compresses the image file to save disk space. As when working with archivers, at this stage of image creation you need to select the degree of compression of the image file. Creating an image without compression will allow you to access files stored in the image almost without delay when working with the image, but the size of the image file will be equal to the space occupied by the files on the partition or hard drive from which the image is taken. Using maximum compression significantly reduces the size of the image file, but increases the time it takes Acronis TrueImage to create it. Clicking the Next button will open the next wizard window. Figure 27.(Image protection with password) At this stage, the wizard offers to protect the created image with a password. The password will restrict access to the files saved in the image; however, if the password is forgotten, it will make recovery from the image impossible. On the next screen, the wizard will prompt you to enter a description of the image being created. A very useful function if there are several images. The next screen contains a summary of the settings that were specified when creating the job. This information allows you to double-check that the settings are correct, and if an error is found, you can correct it by returning to the specific wizard screen using the Back button. The image creation process is started using the Proceed button on the last screen of the Image Creation Wizard. Information about the progress of the task can be obtained in the program window. Figure 28. (Program information window) The Hide button allows you to minimize the window to the tray and close the main program window. This frees up about 15 megabytes of memory. Information about the progress of a task minimized to the tray can be obtained by moving the mouse pointer to the program icon in the tray. The tooltip will display the percentage of completion of the task. During image creation, the TrueImage service occupied approximately 59 megabytes random access memory and 57 megabytes of virtual. The processor load was 99%, but it was possible to work on the computer without problems, since when other applications were active, the TrueImage service ceded resources to them. When the image is created, an information message about this will be displayed on the screen. Restoring from an image occurs using a wizard that can be called double click Click the Restore image icon in the main program window. Figure 29. (Image Recovery Wizard) In this window you need to indicate the image from which you want to restore. After pointing to the image file, the wizard window will display all the information about this image: when it was created, from which partition or disk, the size of the image file and the total size of the files stored in the image after they are extracted to disk. Once the image file from which you want to restore is selected, you need to click Next. Figure 30. (Selecting a partition to restore) If the image contains several partitions or hard drives, then among them you should select those that require recovery. At this stage, the data that will be restored is selected. After clicking Next, the window shown below will open. Figure 31.(Selecting a hard drive for recovery) This window displays a list of all hard drives installed in the system and all partitions that have been created on each drive. It is necessary to select the disk or partition where you want to restore the data selected in the previous step. The disk on which the data will be written can be any disk, not just the one from which the data was placed in the image. After clicking Next, the following window will open. If partitions have been created on the disk to which you want to restore data, the wizard will ask you to confirm their deletion. It should be understood that if you agree to delete partitions on your hard drive and then write information from the image onto it sector by sector, the likelihood of recovering data stored on deleted partitions is practically zero. Therefore, before confirming the removal of partitions, it is better to use the wizard’s recommendation and make sure that the disk on which the image will be written is selected correctly. After clicking the Next button, Acronis TrueImage will block access to the disk or partition to which the image will be deployed. TrueImage allows you to schedule the recovery of several partitions or hard drives at once. If this is required, then by setting the switch to Yes, I want to recover another partition or hard drive and by clicking Next, you can repeat the steps described above and schedule other partitions or hard drives for recovery. If there is no need to restore other partitions or hard drives, then the switch should be set to No, I don’t want to and click Next. A window will open with summary information about the created recovery task. Before starting the task, it makes sense to double-check that all settings are correct. To start the task, click the Start button. The progress of the data recovery task can be monitored in the same window as when creating the image. During image restoration, the TrueImage service used approximately 21 megabytes of RAM and 24 megabytes of virtual memory for its needs. The processor load was approximately 50% and decreased significantly when other applications were active. This allowed us to work comfortably while restoring data from the image, without experiencing a decrease in system performance. When the recovery is complete, an information message is displayed on the screen. Acronis TrueImage now offers the ability to connect partitions stored in an image file as a logical drive. After connecting, another letter will appear in My Computer, and when accessed, the contents of the section will open. By connecting the partition stored in the image as a logical drive, you can copy files from it. But it is impossible to add files to the image or rename them, as well as remove files from the image. Mounting a partition is carried out using a wizard, which can be called by double-clicking on the Mount image icon in the main program window. In the wizard, you need to select the image containing the partition that you want to connect and click Next. In the window that appears, you need to select a letter that will be assigned to the connected partition stored in the image. If you need to connect several partitions, you need to select them one by one and assign each one its own letter. After clicking the Next button, a window will open in which the information collected by the wizard will be displayed. Clicking the Proceed button will complete the wizard and connect the specified partitions to the specified letters. Once the connection is complete, an information message will be displayed on the screen and an Explorer window will automatically open with the contents of the connected section. After connecting the partition from the image to it, you can open general access over the network. To disconnect an image of a partition that was previously connected as a logical drive, you need to use the Dismount Image Wizard. You can call this wizard by double-clicking on the Disconnect image icon in the main program window. To disconnect previously connected partitions stored in the image, just select them in this window and click Next. After clicking the Proceed button in the next window, the drive letter will be freed and the partition image will be disabled. Thus, by mounting certain partitions stored in the image, you can restore files and folders in the state in which they were placed in the image. Acronis TrueImage provides a hard drive cloning feature. Disk cloning is the creation of an exact copy of one disk on another. Most often, cloning is used when replacing one hard drive with another, for example, when the capacity of the old hard drive is small or the new drive has higher performance. When cloning, all information from one disk is rewritten sector by sector to another, which ensures the functionality of the operating system and software on the new disk. This eliminates the need to waste time installing and configuring the system and programs on a new hard drive. To launch the Disk Clone Wizard, you need to double-click on the Clone Disk icon in the main program window. TrueImage has a tool that greatly facilitates the process of partitioning and hard formatting disk. To use this wizard, you need to double-click the Install a new disk icon in the main program window. TrueImage, to automate the creation of images, has a special scheduler. The scheduler helps automate the creation of images of specific sections on a schedule. To launch the Scheduler, double-click on the Assign task icon in the main program window. The image creation wizard will be launched, the settings of which were discussed in detail above. After setting up the image creation, the Scheduler will display a window with a schedule for the operation, where you can select on which days the copying will be carried out. TrueImage has a number of special service functions and settings. Acronis Secure Zone is a space on your hard drive reserved by TrueImage in which the program saves images of partitions or disks. Only TrueImage has access to this zone and therefore it is impossible to accidentally delete or corrupt the image file. Acronis TrueImage creates a protected area on your hard drive where you can save images. If the option Enable Startup Repair is enabled on the last screen of the wizard, then to restore it, you will only need to press the F11 key before Windows boots and after that TrueImage will launch. After launch, you can perform standard operations: creating or restoring disks or partitions from an image. Using the same menu item, you can change the size of a previously created security zone or delete it altogether. Start-up recovery - once a recovery zone has been created, selecting this menu item the next time you restart the computer before loading the operating system, activates the loading of the TrueImage console, with which you can restore data from the image. Checking the image - Sometimes there is a need to check the image file for integrity and make sure that, if necessary, recovery from this file is possible. The Image Verification Wizard helps you check the image file. Working with this wizard comes down to specifying the image file, after which, using the Proceed button, the image check will be launched. Upon completion of the check, TrueImage will display an information message with the result of the file check. The Boot Disk Creation Wizard, which can be launched using the Create Boot Disk shortcut in the Tools section of the main program window, simply creates a bootable CD or a set of floppy disks. They will an indispensable tool to restore partitions or a hard drive from an image in case of serious accidents when the main hard drive fails. It's very easy to create discs by answering the wizard's questions. If you plan to create a bootable CD, then your computer must have a CD-RW drive installed; if you are creating floppy disks, you will need either 6 or 2 of them, depending on the version of TrueImage that will be recorded on them. IN full version drivers will be recorded on the media to support a wide variety of types of hard disks and media. Once the disk or disks have been created, you can boot from them and perform standard operations to restore disks or partitions from an image or to create an image. Work log. All events that occur during TrueImage operation are logged in the operation log. Overall, Acronis TrueImage is quite powerful tool to create backup copies of data. But the functionality of the program is quite limited. Lack of online support indicates that this product is suitable for home use, or use in small businesses. Four copying and restoration attempts were made and all of them were successful. 5. Application and comparison of the reviewed software products Unfortunately, neither reliable equipment nor licensed software does not guarantee 100% data security. There are a lot of reasons that can lead to data loss: a banal failure of the hard drive, a file system failure, file damage by viruses, unwanted changes or deletion of data by the users themselves. You can also lose information as a result of a fire, computer theft, etc. In other words, the possibility of information loss was, is and will always be. The only way to prevent data loss is to back up your data. This method is relevant not only within an enterprise, where data backup and recovery is performed by one or more servers controlled by system administrators, where employees do not have to worry about this, but also at home, as well as in computer classes and Internet cafes. In such places, expensive software and hardware solutions will not pay for themselves, and require serious knowledge and certain user qualifications, but inexpensive, simple, easily customizable applications that would allow information recovery in critical situations are appropriate. The work examined in detail software products aimed at preserving important information, user data and the operating system as a whole. The capabilities of both free software from GFI, which recently began its research in this area of information security, and the capabilities of paid software from companies that have long established themselves in this area - Paragon and Acronis - were considered. Based on the work done, we can compare the functionality of the considered programs. Table 1. Comparison of functionality of data backup programs. Program functions GFI BackupParagon Drive backup WorkstationAcronis TrueImageSupport for the latest hardware+++P2P OS setup-++Incremental update Support is claimed, but not functional++Decremental update+++Archive data storage policy wizard+++P2V Copy/Restore-Requires additional plugin-Connection virtual disk-++Archiving to an FTP/SFTP server+++Password protection of file archives+++Remote program management via an additional Web client+-Availability of emergency boot images-++All functions are collected in a single interface++-Oriented towards inexperienced users users+-+Organization of work Step-by-stepStep-by-stepUse of special. mastersUse of resourcesMinimumMinimumThe activity of other programs is taken into account,minimumCost of the productFreeRUR 1,490 RUR 1,700 Conclusion The constantly growing demand for computer equipment and the global computerization of society are currently not accidental. More and more various services are provided to the population using electronic terminals, the main part of which is Personal Computer. A lot of tasks for managing various processes in production, organizing work and monitoring public transport, and organizing transportation are also assigned to computers. If a failure occurs in some chain, the consequences may be unpredictable. Therefore, the issue of protecting and backing up information is currently quite acute. Further development of technology and informatization will entail a strong increase in the amount of stored information. Therefore, research in the field of information storage and backup is currently in great demand, and will continue to develop in the future, and software products will be improved and adapted to the needs of society.
...a modern data center. If in 2000-2001 the volumes of funds invested in storage systems were approximately...
Igor Zubal,
The material talks about methods of backing up data and includes an overview of the most popular programs.
The job of the smart is to anticipate trouble before it comes...
Some time ago we looked at hard drives: ejecting deleted files, restoration of lost partitions, resuscitation of information after file system destruction. Those who have had to deal with this problem in practice know how unpredictable the result can be. Of course, sometimes information has to be restored by any available means, but it’s still better not to let it be completely lost.
Often huge amounts of information are stored on only one computer hard drive. The PC hard drive itself is far from the most reliable component in the system. Add here cases of user errors, the effects of viruses, failures of the software environment and, finally, the possibility of deliberate destruction of data, and you will understand how vulnerable the information on a computer’s hard drive is. Reliability increases many times over when duplicating, backing up, transferring data to other media, or storing copies of especially valuable information separately.
It would seem that it could be simpler to manually copy information to another medium. Reliable and simple. But this is only at first glance. When there is a lot of data and it is scattered on the hard drive, look for the location necessary files and manually transferring them to backup directories is long and tedious. In addition, the so-called human factor comes into play here: I forgot, I didn’t have time, then I found a more important matter... I had to deal with a company where computers had specially installed pockets for removable hard drives, employees received instructions from management to systematically back up data. And what? Hard drives at this company failed twice; both times the data was not backed up and had to be retrieved from broken hard drives.
You can only hope for some kind of consistency in backing up important data if it is entrusted to the care not of a person, or not only of a person, but of special software or hardware that operates automatically. Let's say special program can automatically back up data to another storage device once an hour, once a day or once a week. The program will do this much faster than a human, since all data will be automatically extracted from predefined sources and collected in in the right place archive directory. Naturally, the safety of backup copies will be guaranteed only when they are transferred to another, preferably removable media. This could be a pocket with a removable hard drive, a CD-R/RW disk, or, in extreme cases, a hard drive on another computer connected via a local network. Such hardware is usually included as standard in PCs and offices.
Brute force method - backing up the entire disk
Backing up an entire logical drive or even a physical drive is the most reliable way to save data. If a system disk is backed up, then along with the data, the operating system is also placed in the archive (image), all installed applications. This saves not only in case of loss of valuable data, but also in case of OS crash and even hard drive failure. Under normal circumstances, if the OS crashes or the hard drive fails, you have to do everything from scratch: install the OS, install drivers, install and configure software. This takes more than one hour, or even more than one day. If you have a reserved copy system disk– in about 10–20 minutes, all the data, a working OS and configured applications will be in place, and the computer will be operational again.
In this case, the program creates a so-called disk image file. Essentially, an image is an archive file, the data in which can be highly compressed; the program that created it can restore the information back to disk, in the same order in which the data was located at the time the image was created.
Acronis True Image
The seventh version has a well-thought-out set of functions for reservation and initially has a Russian interface. The program is installed and can work in Windows environment 98/Me/NT/2000/XP, and also creates its own boot floppy disks and CDs, with the help of which in an emergency you can start and revive a computer with a damaged OS. Acronis True Image creates backup disk images, this process can be automated, and also allows you to clone disks.
In the main window of Acronis True Image, a separate button is provided for each task, which is convenient, then the program goes into wizard mode for each selected process. Disk images can be created in the Windows environment, which is one of the main advantages, or using Acronis True Image boot disks. Restoring images is also nominally possible from Windows, but when resuscitating a system disk, you should use one of the options from Acronis True Image boot disks, which must be created in advance.
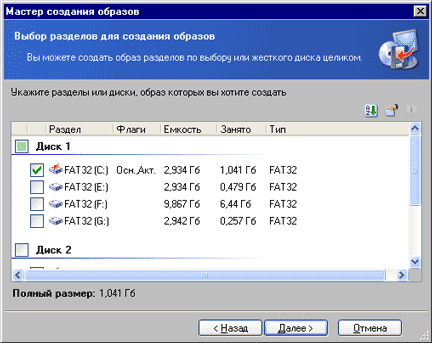
Backup disk images are created in a step-by-step wizard mode (Create Image | Run). The steps of the wizard are typical: first, select partitions for archiving (Fig. 2), then the location of the images; in the next steps, additional backup parameters are set. Images can be saved on another computer via a local network. The wizard provides the ability to split the created image into fragments given size, say, for subsequent recording to CD-R/RW, ZIP or FDD. The ability to create incremental images may be useful. Then, with each subsequent backup of the same disk, a separate complementary (incremental) image will be created, where only changes that have occurred since the previous backup are made. An incremental image has a much smaller volume than the main one, less time is spent on its creation, and disk space is saved. Incremental images are only valid together with the first, main image. Images can be password protected.
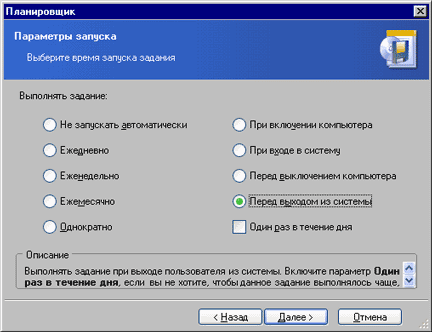
A distinctive feature of Acronis True Image is its convenient task scheduler (Tasks | Assign a task). Here you can set daily automatic disk backups by specifying the starting point for each process (Fig. 3). It is especially practical, in my opinion, to perform a backup before turning off the computer. Then all the data accumulated during the day will be added to the archive when the work is completed. During the standard shutdown procedure in Windows, Acronis True Image will pause this process, display a warning window, perform an archive, and only then turn off the computer. Here it is convenient to use saving data in incremental images, which, if created systematically, will take much less time. With Acronis True Image you can create boot disks on floppy disks or CDs.
Acronis True Image was created by a team of domestic developers (SWSoft-MIPT) and is a commercial product. Also available in Personal and Server versions. The cost of Acronis True Image Personal is very low, but the program cannot work on a local network and there is no automatic scheduled backup option.
It is worth noting that we were always talking about the simplest version without the Personal or Server prefix. Prices different versions product are 4, 50 and 500 dollars respectively.
There are other utilities that allow you to create and restore backup disk images. These include: All of these utilities have a basic set of properties: the ability to write the created image files to different media, including CD-R/RW, they can create bootable floppies and CDs, the created images can be compressed and split into parts. Paragon Drive Backup is supported in Russia and has a Russian-language interface. On the Internet you can find old Norton Ghost for DOS versions 5–6; this is one ghost.exe file 600–700 KB in size, which can be launched not only in DOS, but also in Windows 9X. This file launches a program that can backup images to your hard drive and restore them from your hard drive or CD. Older versions of Norton Ghost do not create their own boot floppies, but the ghost.exe file can be launched using any standard DOS-based boot floppy.
Backup selected jobs
Above we discussed programs for backing up the entire contents of disks into images. This approach has its undeniable advantages, but there are also disadvantages. Backing up an image is only possible for the entire disk, which takes a long time and is not always necessary. You can restore information from an image only using the utility that created it, which, to a certain extent, limits the possibility of free access to the reserved data. With normal copying, you can back up only the specified information; the files are saved in their original form. Below are some utilities that automate the backup process and offer a number of additional functions.
File Backup Watcher
Allows you to create backup copies of files and directories as local computer, and online. The program can also make backups to FTP, E-Mail, record to CD-R/RW, DVD recorder and other types of drives. An automatic operating mode and task scheduling are provided. File Backup Watcher is a commercial product, and much attention is paid to distribution in Russia, Ukraine, and Belarus; the utility has the ability to select Russian and Ukrainian language interfaces.

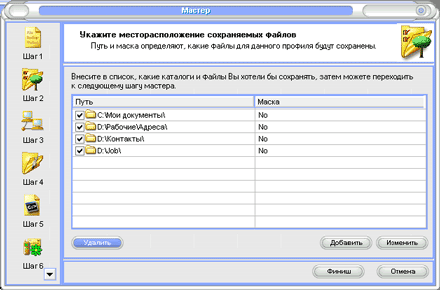
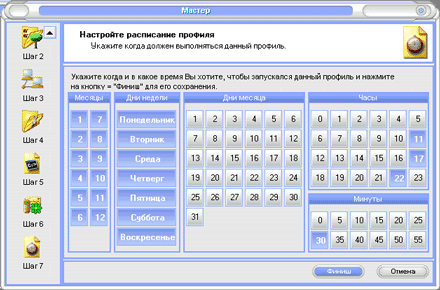
File Backup Watcher is installed in the OS in the usual way and puts itself in startup. Before the program begins to perform its assigned functions, that is, to backup data, you need to create task profiles. A new profile is created along the path (Profile | New | Profile) or from the context menu right button mice. The profile is created in wizard mode, there are seven sequential steps. At the first step, a name is set, the profile is activated, and comments can be added. At the second step, a list of files and directories that are intended for backup is specified (Fig. 5). Next, the type of transportation and the location of the backup data are determined: it can be local or network computer, FTP, E-Mail, CD/DVD recorder. At the fourth step, the backup scheme is set; files for each session can be copied completely, or you can only specify the movement of new and changed files. At the last step, the schedule is configured (Fig. 6), the profile execution is automatically launched according to the specified months, days and times. Moreover, several time points can be specified per day.
vuBrief
Functional and completely free program to automate data backup. can transfer and synchronize files between directories within one computer, synchronize data between remote computers over local network. Archive specified files and folders using a built-in or external archiver. It is also possible to synchronize files between a local directory and an FTP directory. The program has a Russian interface and is equipped with a detailed, illustrated description in Russian.
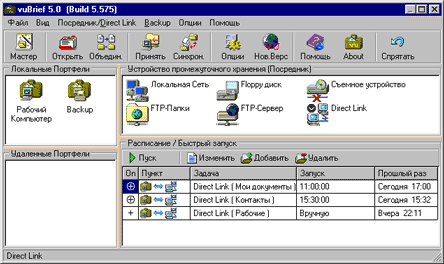
vuBrief, like any other program of this kind, requires the preliminary creation of tasks for backing up data. In its simplest form, the task stipulates from which working directories on the PC the data should be backed up, and in which archive directories it should be placed. It is also necessary to configure the synchronization parameters of the directories between which data will be exchanged during the backup process.
After all, vuBrief doesn’t just copy data from one directory to another, although it can do that too—the program synchronizes the contents of specified directories. Synchronization implies not only the transfer of information from one place to another, but also the ability to exchange and delete files. There can be quite a few synchronization methods, all of them are customizable. It must be taken into account that choosing the wrong synchronization scheme for a particular case can lead to data loss - deletion by the program. Rules for synchronization are defined for each job.

Go to the tasks window by double-clicking on the “Briefcase” shortcut (Work computer), and then on the selected item (Properties | Direct-Link | Synchronization direction, details) (Fig. 8). The most trivial and safest option is to select “as Backup (write only)” - in this case, the usual copying of data from the source folder to the archive directory will occur. The most dangerous can be considered the random selection of the preset item “as Sample (Read-Only)”. In the "like Sample" direction, the reverse movement occurs: from a certain archive directory to the working folder of the computer, while all files in the working folder whose names are not in the archive are simply deleted by default.
Fortunately, all synchronization modes are customizable, you can change only some preset settings, or create your own way of synchronizing directories - in this regard, vuBrief is very progressive. But synchronization is a delicate matter; be sure to first practice with unnecessary data in order to avoid unpleasant consequences later.
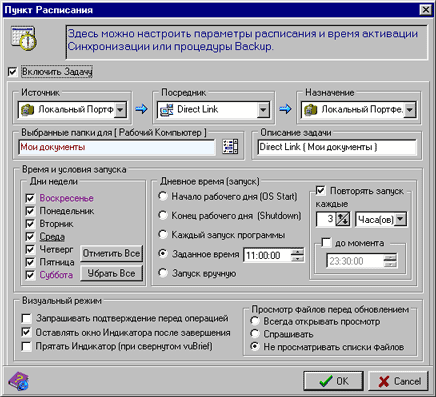
A schedule is created to automatically reserve vuBrief jobs (Fig. 9). You can make a reservation by day of the week, by time of day, after a certain number of hours and when the program starts, of course, provided that the program is already launched and running. The latter is very important, because during installation this program did not put itself in my startup. Its shortcut must be manually placed in the Windows Startup folder, then vuBrief will start working immediately after the OS starts.
Information Backup System
The description of the utility says succinctly: (IBS) is designed to backup information manually or automatically when data changes or according to a specified schedule. It should be noted right away: the program is intended specifically for backup, since synchronization is not included in its capabilities. Archives can be compressed using an external archiver. Backups can be placed both on local and network folders. Information Backup System has a Russian interface, it is a commercial program, but its cost is low.
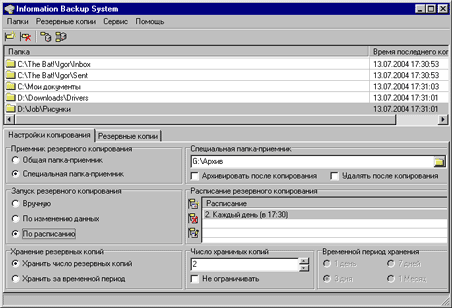
The main window of the Information Backup System contains all its tools (Fig. 10). A list of tasks is formed at the top. Below, for a backup copy of each task, a general or special destination folder is indicated, and a task schedule is set. Reservation can be made manually, by time (Fig. 11), or by the fact of changes in the contents in the task catalogs. The program initially puts itself into autoload, so it constantly monitors the status of its tasks. When reserving by time, the process may begin with some delay - up to two minutes.

Information Backup System backs up each task to a specified directory with a user-specified name, but inside it the program creates an additional subdirectory structure. First, a subdirectory is created, the name of which contains the entire path to the source folder, even with the indication logical drive, then subdirectories are created inside it for each new copy separately. The names of backup subdirectories indicate sequentially: year, month, day and time of their creation. Old copies can be deleted; the settings indicate the number of stored backup copies. This approach does not particularly save space and time, but it looks reliable and understandable; using the names of the catalogs, it is then easy to understand the copies.
Here we can also mention a more highly specialized utility; this program is designed to create and restore mail backups. Declared support for a large number of email clients: Outlook Express, Microsoft Outlook, Eudora (Pro and Light), Netscape Messenger and Netscape Mail, Opera, IncrediMail, Pegasus Mail, The Bat!, PocoMail. The utility has a task scheduler, the ability to automate mail backups, password protection and compression of stored data.
So, two types of programs were discussed above: those that create backup disk images and those that perform regular copying to automatic mode. Which type should you prefer? Both are best. Backing up to an image saves you when the operating system crashes or the working disk is damaged, when you need to quickly restore not only the data, but also the functionality of the computer. The rather lengthy operation of creating images can be performed less frequently, say, only when some serious changes are made to the system, which must be taken into account during its possible restoration. It is worth backing up important data by copying or synchronizing every day. Systematic transfer of selected data will take less time and disk space. In the event of an OS crash or a working drive failure, system functionality can be easily restored by restoring backup disk images. The missing data on them will be immediately filled in from daily backups of the most important files.
The search module is not installed.
Backup technologies
Vladimir Mastitsky, "Polikom Pro"
Introduction
The problem of information security is of great importance in modern business. For example, for any bank, data on transactions carried out over a certain period of time is very important. Similarly, for any trading company, up-to-date information and statistical data on sales of goods, shipments to customers, balances in warehouses, etc. are vital. and so on. Countless examples can be given. To ensure the safety of information in modern corporate information systems, critical business data is regularly backed up. For this purpose, special hardware and software backup tools are used.
As business develops, the volume of stored data also grows. According to analysts, the volume of corporate data is increasing annually by at least 60%. Accordingly, the requirements for the technologies and backup systems used are increasing.
The purpose of this article is to introduce the reader to modern backup technologies. Let's hope that after reading it, the reader will gain some understanding of these important and necessary technologies.
General information about backup technologies
Purpose
Hardware and software backup tools are designed to create copies of data necessary to restore the functionality of a corporate information system in the event of an emergency or other unforeseen circumstances. If you have a backup copy, you can quickly restore the state of the corporate system at the time of the last backup (that is, after restoration, all changes that have occurred in the system since the last backup are lost).
Typically, a backup covers all data located on hard drives(as we remember, this is the first level of the hierarchy of data storage systems), including various system and service information. The devices and backup systems themselves are located at the second and third levels of corporate data storage systems. This structured design is intended to reduce the cost of storing rarely used information, since files that have not been accessed by users for a long time are usually automatically moved to lower levels of media (the value of this period of time is set by the system administrator). In this case, the movement of files is organized in such a way that the volume free space on server hard drives was maintained at a given level.
Over the past few decades, leading industry manufacturers have put a lot of effort and invested huge amounts of money into developing backup technologies, systems, and related media. Currently, the global market for backup products and systems is characterized by significant diversity in the range of technologies and solutions offered.
Main types of backup devices and systems
There are several main types of backup devices and systems designed for use in both small businesses and large corporations with distributed branches. They all differ from each other in a number of characteristics and, not least, in the degree of automation of backup operations.
Currently, the most common backup hardware is tape devices and systems, which have completely changed as technology has advanced. They have increased the speed of writing/reading data several times (now reaching tens of megabytes per second), capacity (a modern magnetic tape cartridge can already hold many hundreds of gigabytes!), reliability and fault tolerance. Currently there are following types tape devices and backup systems:
Tape drives (streamers) that write (and read) information onto a cartridge that replaces the traditional reel of magnetic tape.
Stackers, which are now, however, being used less and less due to their lack of flexibility in operation. The stacker contains one tape drive and several cartridges. At the same time, the cartridges are installed in a stacker in special trays and fed into the streamer in a strictly established order using a special robotic mechanism for replacing cartridges.
Next in the hierarchy of tape storage devices (according to their complexity) are autoloaders, which to a certain extent resemble a stacker (usually they have one tape drive installed, as well as several cartridges - up to 10 in total). A distinctive feature of autoloaders is the ability to feed cartridges (placed in a special magazine) in a random, rather than rigid, order. The frequency of changing cartridges can be set, for example, determining the daily replacement of cartridges.
Tape libraries are even more complex tape backup solutions, consisting of systems that include many cartridges and up to several tape drives (which significantly increases the speed of backup and recovery). The library consists of compartments in which cartridges are stored, and a mechanism for changing cartridges (jukebox) in streamers. Accordingly, there are two schemes for loading cartridges using a robotic mechanism. When using the first scheme, any cartridge is loaded into any streamer. In the second scheme, each streamer works only with specific cartridges. Most important characteristics tape libraries are data transfer speed, capacity and reliability. Tape libraries differ from each other in such characteristics as the number of slots for cartridges and the number of tape drives, the number of ports for accessing cartridges, the list of supported operating systems, as well as the capabilities of built-in management functions. Libraries are very powerful backup solutions that allow you to back up huge amounts of data (reaching hundreds of terabytes) at high speed.
RAIT arrays (Redundant Arrays of Independent Tape) are so-called arrays of redundant streamers (they are also called redundant arrays of independent streamers). The RAIT array housing contains several tape drives, each of which works with only one cartridge at a time, thereby significantly increasing backup speed and fault tolerance (the RAIT array is created based on the RAID specifications used for disk subsystems). True, RAIT arrays pay for high speed and reliability with low capacity and the impossibility of automatically changing (so-called rotation) media. It should be said that RAIT array technology can also be defined using software, grouping autoloaders or tape libraries.
In addition to tape, there are other types of backup devices and systems that work with other types of storage media (primarily magneto-optical and optical). For example, magneto-optical and optical libraries are quite widespread, the advantage of which is the huge life cycle of their cartridges (several million records/rewrites) and long service life (more than 30 years). The disadvantage of magneto-optical libraries is the relatively small storage capacity (only a few gigabytes). There are also libraries based on CDs and DVDs.
It is impossible not to say a few words about NAS servers, which can be considered a fairly successful solution in the field of backing up important data. At the same time, the data transfer speed in a NAS server is much higher than in tape systems and backup devices. Disk systems that are sometimes used to store important data include RAID arrays (arrays of independent redundant disks).
For backup, the capabilities of SAN storage network technology are also used, which can significantly speed up the backup of important data through the consolidation of devices and storage systems, as well as the possibility of off-network and off-server backup.
However, at present, the most common devices and backup systems are still associated with storing information on magnetic tape (although talk about ousting magnetic tapes from the market began back in 1972, immediately after the appearance of the first hard drives).
Main types of magnetic tape formats
All existing tape devices and backup systems are based on two technologies: linear recording (recording with a fixed magnetic head) and slanted recording. The roots of these technologies grow from analog magnetic recording technology (used in the EU series NML). They differ from each other mainly in the method of recording data with magnetic heads and the speed of movement of the magnetic tape (the service life of the magnetic tape and the data access time depend on this).
The main manufacturers of linear recording backup devices and systems are Tandberg Data and Quantum. At the same time, Tandberg Data produces streamers and tape libraries for the DLT format, and has also developed SLR technology based on 0.25" tapes (QIC).
DLT streamers use a 0.5" wide magnetic tape and a single-reel cartridge (the take-up drum is non-removable and is located in the device itself). The entire volume of the cartridge is filled with magnetic tape. DLT technology is based on a multi-channel method of working with magnetic tapes - high speed of working with tapes is achieved in account for simultaneous reading or writing of several heads of the device. DLT technology is now most common in backup systems of mid-level and above. Since the fall of 2000, DLT1 format tape drives have also appeared on the market.
There is also a SuperDLT (SDLT) format. SuperDLT devices use a different, more advanced magnetic tape, different magnetic heads, an optical track positioning system, etc. SDLT devices cannot work with DLT cartridges due to their design features.
In turn, SLR streamers use 0.25" wide magnetic tape located in a completely enclosed, reliable cartridge.
At the end of the 90s. A promising format for recording on magnetic tape was developed - LTO (Linear Tape Open). It was created jointly by IBM, HP and Seagate and is now quickly gaining popularity. It should be noted that the LTO format was not developed based on any existing backup solution. The first LTO format streamers were released in December 2000, and starting in January 2003, second-generation LTO streamer models appeared on the market. In fact, LTO is a variant of bidirectional multi-channel linear recording technology that uses a 0.5" wide magnetic tape. It should be said that there are two variants of LTO technology:
Accelis streamers entry level with a two-reel cartridge, which provide minimum access time and maximum speed.
Mid-level Ultrium streamers with maximum capacity. The design of Ultrium and DLT cartridges and tape drives is, in a certain sense, similar. An interesting and useful feature of the Ultrium Generation 1 cartridge is the microchip built into it, which records all the data about the recorded files and their location, as well as statistics on the use of the cartridge.
The plans for the development of LTO technology include achieving by 2007 (Ultrium 4 is already standard) a cartridge capacity of 800 GB (uncompressed data) and a data transfer speed of up to 160 MB/s (also uncompressed data). For comparison, LTO Ultrium 2 streamers with a cartridge capacity of 200 GB and a data transfer speed of 35 MB/s have now appeared on the market.
There is also the Travan format, which uses a magnetic tape width of 8 mm. The authors of the Travan specification are Conner, IOmega, HP, 3M and Sony.
When using the horizontal-slant magnetic recording method (it was developed for analog video recorders by Ampex back in the mid-50s), the magnetic tape is pulled at a speed of several centimeters per second past a cylinder rotating at high speed, on which the read-write heads are attached . This makes possible a high relative speed between the magnetic tape and the head. Using this method It is possible to work with thinner magnetic tapes. In addition, the track density is several times higher than with linear recording.
For slant-line recording technology, two main types of streamers have been created, differing in the width of the magnetic tape in the cartridge - 4 mm and 8 mm. 4 mm streamers use DAT (Digital Audio Tape) technology, developed by Sony in 1989. There are several generations of tape backup devices with DAT technology implemented in them: DDS-1 (Digital Data Storage), DDS-2, DDS- 3 and DDS-4 (DDS-5 format also appeared).
The technology of analog slant-line and then digital recording on 8 mm wide magnetic tape was developed in the 80s. also by Sony. Currently on the market there are 8 mm streamers from Exabyte (Eliant, Mammoth, Mammoth-2 formats), Ecrix (VXA format) and Sony (AIT - Advanced Intelligent Tape, AIT-2, AIT-3, S-AIT - Super formats Advanced Intelligent Tape).
This a large number of formats naturally leads to mutual incompatibility between tape devices and backup systems. In addition, all tape drives and, accordingly, autoloaders and tape libraries based on them, currently on the market, differ from each other in many characteristics (capacity of the cartridge and the entire system, performance, cost, reliability, etc.). Each of them has its own advantages and disadvantages (the common one being the incompatibility of cartridges of different formats). In fact, each tape device or system is best suited for a specific application.
Basic Backup Methods
Backup methods for disk storage systems and tape storage systems differ from each other. Let's first look at copying methods for disk systems.
The technology of backing up to disk using the so-called “cloning” (point-in-time) is quite popular. Disk “cloning” is offered in their solutions by companies such as XIOtech, IBM, EMC, etc. The essence of cloning is that for backup purposes, several physical copies of volumes (clones) are created daily. After creating the first full copy, only the changed data is subsequently recorded, which significantly reduces the disk backup time (there is no need to re-write the entire volume). If it is necessary to restore data, access is made to the latest current copy. The disadvantage of cloning technology is the need for a significant amount of disk space.
There is also a variant of cloning technology called snapshot. Snapshot backup technology is implemented in solutions from IBM, Network Appliance, StorageTek, etc. When used, logical copies of the snapshot state of volumes or files are created. These two technologies differ from each other in that cloning actually creates a separate physical copy of the disk, while instant copying creates a logical copy (simulating a physical copy). A disk image is created, no data is transferred, no additional memory is needed, and the entire instant copy procedure occurs almost instantly. The disadvantage of instant copy technology is its inability to protect data from physical loss.
In turn, tape backup can be full, incremental and differential.
A full backup creates a complete (as the name suggests) copy of your data. The advantages of this method are greater reliability and relatively quick recovery of information (for this, only one recorded image is sufficient). The disadvantages of the method are the long duration of the procedure and significant consumption of magnetic tape.
Incremental tape backups only duplicate files that have been created or changed since the last backup. That is, in any case, a full copy is first created, and during subsequent backup procedures, only new or modified files (relative to the last copy) are backed up. The advantages of the incremental method are its high speed and minimal magnetic tape consumption. The disadvantage of the incremental method is the length of time it takes to restore information, since it is restored first from a full copy, and then sequentially from all subsequent copies.
With differential backup, only new or changed files are also duplicated, but relative to the last full backup. Accordingly, as the number of differential backup procedures increases, its duration also increases. However, to restore data you will only need a full copy and the latest differential copy.
In practice, full data backups are usually performed regularly and incremental or differential backups are performed daily.
Manufacturers
The market for backup devices and systems (and media for them) is developing steadily from year to year. According to forecasts of various analysts, its volume annually amounts to several billion dollars (according to IDC, only for tape drives with 4/8 mm magnetic tape and DLT - $2.9 billion in 2003).
Accordingly, this market attracts the attention of both many well-known companies and fairly little-known companies (often specializing in the manufacture of various components for complex backup solutions). There are many dozens of companies participating in this market. The most famous of them include Seagate LTO, Tandberg, IBM, etc.
It should also be noted that a large variety of special software tools have been developed to manage devices and backup systems, the market volume of which also amounts to many billions of dollars. Among the developers of backup management software, industry analysts especially highlight Yosemite Technologies, Seagate Software, Legato Systems, Veritas, Computer Associates, BakBone, IBM Tivoli, HP, EMC, etc.
Benefits of Backup Technologies
When analyzing the benefits of modern backup technologies, it is necessary to consider disk and tape technologies separately.
So, what are the main advantages of disk systems? First of all, of course, it is the high speed of reading and writing data and random access to data.
In turn, DVD discs have the advantages of relatively high performance, random access to data and a fairly low cost of media.
The advantages of CDs are low cost of media and random access to data.
Accordingly, libraries based on all these media are also quite different high performance and relatively low cost.
In turn, streamers are distinguished by the low cost of both the entire device and the carrier - magnetic tape. Currently, tape devices have the lowest unit cost for storing large amounts of information. In addition, they have a fairly significant information storage capacity.
Tape libraries are created on the basis of tape drives, which have serious advantages.
Firstly, they have a large storage capacity (after all, the capacity of just one cartridge is hundreds of gigabytes).
Secondly, due to the fast, automated change of cartridges, they are able to process huge amounts of information.
Thirdly, automation of backup operations in robotic tape libraries eliminates the influence of the human factor (and, accordingly, errors during backup).
And, fourthly, tape libraries are much cheaper than disk backup systems.
It's safe to say that tape devices and storage systems are the most versatile and inexpensive means of backup and recovery today.
Disadvantages of Backup Technologies
Currently used backup technologies also have their drawbacks.
The main disadvantage of disk systems used for backup purposes is their high cost (however, recently the cost of storing a megabyte of memory on hard disks has been rapidly falling, provided that the overall capacity of disk backup systems increases).
In turn, tape devices and backup systems also have many disadvantages.
Firstly, the lack of a unified magnetic tape recording format in some cases interferes with the creation of heterogeneous data storage systems (manufacturers are trying to solve the problem of format incompatibility throughout the industry, in particular, by establishing the Enhanced Backup Solutions Initiative).
Secondly, they have relatively slow backup/restore speeds (which can result in a full backup process taking many hours).
Thirdly, due to the use of a sequential access method, they are characterized great importance time of access to the necessary information (after all, the tape still needs to be rewinded to the required place...). That is, tape devices and backup systems are clearly not suitable for online storage and processing of information (but this, strictly speaking, is not their purpose, but disk storage systems).
Fourthly, when storing cartridges, you must comply with certain temperature regime and maintain a given level of humidity, and during long-term storage, magnetic tapes require periodic rewinding to relieve internal stress.
Fifthly, if you need to access many small files, due to intensive rewinding, magnetic tapes and heads quickly wear out.
Options for using backup technologies
Each device and backup system has its own area of application.
For example, disk backup systems are used for online backup and data recovery. As a result, they are used in cases where rapid data recovery is necessary (for example, in billing systems).
When it comes to tape devices and systems, the industry consensus is that they are most effective for solving streaming data problems, of which the main ones include:
Backup and disaster recovery;
Reliable long-term storage of large-capacity data archives;
Storing multi-gigabyte files (for example, in CAD applications).
It should be said that the areas of application of backup devices and systems are quite diverse, since the number of applications in which it is necessary to save critical data increases every year. Such applications include, in particular: multimedia, video-on-demand, medical image processing, Web publishing, disaster-proof data protection, etc. (not to mention corporate storage and databases, storage of large-sized graphic files CAD, archives Email, as well as billing and banking transaction systems, etc.). The continued increase in the speed of data backup/restoration in tape systems allows them to be used in data mining applications.
At the same time, tape libraries are best used in enterprise-level storage systems, since at a relatively low cost they are capable of storing huge amounts of data. Tape libraries are especially effective for centralized backup in heterogeneous environments where common system storage (remember the advantages of SAN). In this case, their main advantages are most fully demonstrated - very high speed of copying and restoring information (many hundreds of gigabytes per hour), large capacity (reaching hundreds of terabytes), high storage reliability and minimal unit cost of storage (per megabyte of data). Tape arrays (RAIT) are used for mission-critical backup operations.
In turn, in small and medium-sized enterprises, the possibility of using a full-featured, large-capacity tape library must be considered specifically for each case. If the load level of a library with dozens of cartridges is small, it is hardly advisable to buy it (you can probably get by with an autoloader).
Tape drives are used for backing up small amounts of information in small businesses and, in some cases, for backing up at home - from desktop personal PCs.
conclusions
1. Backup devices and systems occupy an important place in corporate data storage systems.
2. Modern technologies backups are quite complex and feature a significant variety of formats, methods, devices and systems used.
3. Considering the complexity and diversity of existing backup technologies, when creating a multi-level corporate data storage system that is optimal in price and functionality, it is necessary to focus on the successful experience of implementation and practical application of such systems at various enterprises and organizations, and the help of an experienced system integrator will not be superfluous .
|
In the original or new location in case of damage or destruction.
Encyclopedic YouTube
1 / 5
Video #57. Backup on Windows 10
Lesson 12 - Backup
8. LINUX. Backup | Technostream
AOMEI Backupper Standard - system backup and recovery
Reserve copy of Windows 10
Subtitles
Name of operations
- Data backup (data backup) is the process of creating a copy of data.
- Data recovery is the process of restoring it to its original location.
Target
Backup is necessary to be able to quickly and inexpensively restore information (documents, programs, settings, etc.) in the event that a working copy of information is lost for any reason.
In addition, the problem of data transfer and working with common documents is solved.
Backup system requirements
One-time copy
The simplest scheme that does not involve media rotation. All operations are carried out manually. Before copying, the administrator sets the backup start time and lists the file systems or directories that need to be copied. This information can be stored in a database so that it can be used again. For one-time copying, full copying is most often used.
Simple Rotation
Simple rotation implies that a certain set of tapes is used cyclically. For example, a rotation cycle may be a week, in which case a separate media is allocated for a specific working day of the week. The disadvantage of this scheme is that it is not very suitable for maintaining an archive, since the number of media in the archive is rapidly increasing. In addition, incremental/differential recording is carried out on the same media, which leads to significant wear and tear and, as a result, increases the likelihood of failure.
"Grandfather, father, son"
This scheme has a hierarchical structure and involves the use of a set of three sets of media. Once a week a complete copy of the computer disks is made ( "father"), incremental (or differential) copying is carried out daily ( "son"). Additionally, once a month another full copying is carried out ( "grandfather"). The composition of the daily and weekly set is constant. Thus, compared to simple rotation, the archive contains only monthly copies plus the latest weekly and daily copies. The disadvantage of this scheme is that only the data available at the end of the month, as well as wear and tear of the media, are included in the archive.
"Tower of Hanoi"
The scheme is intended to address some of the shortcomings of the simple rotation and Grandfather, Father, Son rotation schemes. The scheme is based on the use of several sets of media. Each set is designed for weekly copying, as in a simple rotation scheme, but without removing full copies. In other words, a separate set includes media with a full weekly copy and media with daily incremental (differential) copies. The specific problem of the Tower of Hanoi scheme is its higher complexity than other schemes.
"10 sets"
This scheme is designed for ten sets of media. The period of forty weeks is divided into ten cycles. During the cycle, each set is assigned one day of the week. After a four-week cycle, the set number is shifted by one day. In other words, if in the first cycle dial number 1 was responsible for Monday, and number 2 for Tuesday, then in the second cycle dial number 2 was responsible for Monday, and number 3 for Tuesday. This scheme allows you to evenly distribute the load, and therefore wear between all media.
Schemes "Tower of Hanoi" [ ] and "10 sets" are used infrequently as many backup systems do not support them.
Backup storage
- Streamer tape - recording backup data onto the magnetic tape of the streamer;
- “Cloud” backup - recording backup data using “cloud” technology through online services of special providers;
- DVD or CD - recording backup data onto compact discs;
- HDD - recording backup data on a computer hard drive;
- LAN - recording backup data to any machine within the local network;
- FTP - recording backup data to FTP servers;
- USB - writes backup data to any USB-compatible device (such as a flash card or external hard drive).
Reasons for losing information
Operational failures of storage media
Description: random breakdowns within the failure statistics associated with negligence or exhaustion of the resource. If important information has already been lost, you can contact a specialized service, but the reliability is not one hundred percent.
Solution: store all information (each file) in at least two copies (each copy on its own storage medium). For this purpose:
- disaster proxy server in such a way that updates are cached (these are all measures to reduce traffic).
- Have copies in a place where the virus cannot reach - a dedicated server or removable media.
- If copying goes to the server: ensure that the server is protected from viruses (either install an antivirus or use an OS for which the likelihood of infection is low). Keep versions old enough for a copy to exist that has not come into contact with an infected computer.
- If copying is to removable media: store some of the media (without writing to it) long enough for a copy to exist that has not come into contact with the infected computer.
- Use of write-once media: CD-R, DVD-R, BD-R. Their volume is insufficient for serious applications.
Human factor
Description: intentional or unintentional destruction of important information - by a person, specially written malware or faulty software.
- Carefully set rights to all resources so that other users cannot modify other people's files. An exception is made for the system administrator, who must have all rights to everything in order to be able to correct errors of users, programs, etc.
- Build a working backup system - a system that people actually use and that is sufficiently resistant to operator errors. If the user does not use the backup system, all responsibility for safety falls on him.
- Keep versions old enough so that if corrupted data is discovered, the file can be restored.
- Before reinstalling the OS, be sure to copy the entire contents of the partition on which the OS will be installed to the server, to another partition, or to a CD/DVD.
- Promptly update software that is suspected of data loss.
